Final Lecture: Course Overview
... End-to-End Principle Whenever possible, communications protocol operations should be defined to occur at the end-points of a communications system. ...
... End-to-End Principle Whenever possible, communications protocol operations should be defined to occur at the end-points of a communications system. ...
Expanded Notes: Network Monitoring Parts 1 and 2
... Syslog. Syslog is a non-Microsoft log that was developed in the 1980s. It provides devices that normally wouldn't be able to communicate with the means of delivering performance and problem information to system administrators. This permits there to be separation between the software that generates ...
... Syslog. Syslog is a non-Microsoft log that was developed in the 1980s. It provides devices that normally wouldn't be able to communicate with the means of delivering performance and problem information to system administrators. This permits there to be separation between the software that generates ...
What Is an Enterprise Session Border Controller? An Oracle White Paper
... conventional private branch exchange (PBX) systems with Voice over IP (VoIP) and Unified Communications (UC) solutions and cloud-based services to improve collaboration and productivity, as well as to contain capital and operating expenses. Today’s mobile information professionals are no longer teth ...
... conventional private branch exchange (PBX) systems with Voice over IP (VoIP) and Unified Communications (UC) solutions and cloud-based services to improve collaboration and productivity, as well as to contain capital and operating expenses. Today’s mobile information professionals are no longer teth ...
Application of Networks
... Good compromise over the other two topologies as it allows relatively high data rates. If a node goes down, it does not affect the rest of the network. Disadvantages: Requires a network protocol to detect when two nodes are transmitting at the same time. Does not cope well with heavy traffic rates. ...
... Good compromise over the other two topologies as it allows relatively high data rates. If a node goes down, it does not affect the rest of the network. Disadvantages: Requires a network protocol to detect when two nodes are transmitting at the same time. Does not cope well with heavy traffic rates. ...
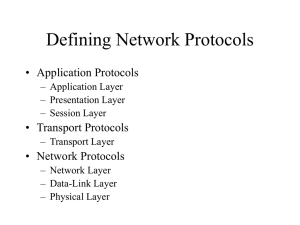
Defining Network Protocols
... Associates an ethernet address to an IP address arp -a or multi show/arp only local (router port) addresses shown ARP entries have a finite (timed) lifetime ARP entries are created by routers for non ethernet protocols (token ring, PPP) • tracing an ethernet address – Host system – Router – Switch ...
... Associates an ethernet address to an IP address arp -a or multi show/arp only local (router port) addresses shown ARP entries have a finite (timed) lifetime ARP entries are created by routers for non ethernet protocols (token ring, PPP) • tracing an ethernet address – Host system – Router – Switch ...
Components of Intrusion Detection System
... – E.G., BSM on Solaris: logs all direct or indirect events generated by a user – strace for system calls made by a program ...
... – E.G., BSM on Solaris: logs all direct or indirect events generated by a user – strace for system calls made by a program ...
internet use in Calgary
... must agree to the terms of the agreement before the order is processed. The AAS will monitor network traffic and disconnect any devices that appear to be causing overall network problems. Order Items ...
... must agree to the terms of the agreement before the order is processed. The AAS will monitor network traffic and disconnect any devices that appear to be causing overall network problems. Order Items ...
ppt
... delay within the communications subnet} This delay is the sum of the delays on each subnet link traversed by the packet. Each link delay consists of four components [Bertsekas and Gallager]: Networks: Introduction ...
... delay within the communications subnet} This delay is the sum of the delays on each subnet link traversed by the packet. Each link delay consists of four components [Bertsekas and Gallager]: Networks: Introduction ...
Rutgers IT Complex
... Copyright Michael R Mundrane 2001. This work is the intellectual property of the author. Permission is granted for this material to be shared for noncommercial, educational purposes provided that this copyright statement appears on the reproduced materials and notice is given that the copying is by ...
... Copyright Michael R Mundrane 2001. This work is the intellectual property of the author. Permission is granted for this material to be shared for noncommercial, educational purposes provided that this copyright statement appears on the reproduced materials and notice is given that the copying is by ...
Lecture 1 Installing Linux, VMware, Reconnaissance, Network
... • TCP Connect -- attempt to complete 3-way handshake, look for SYN-ACK, easy to detect this scan • TCP SYN Scan -- “half-open” scan, look for SYN-ACK, then send RESET, target system will not record connection, also faster than TCP connect scan • TCP FIN, Xmas Tree, Null Scans -- scans that violate t ...
... • TCP Connect -- attempt to complete 3-way handshake, look for SYN-ACK, easy to detect this scan • TCP SYN Scan -- “half-open” scan, look for SYN-ACK, then send RESET, target system will not record connection, also faster than TCP connect scan • TCP FIN, Xmas Tree, Null Scans -- scans that violate t ...
P4P: Proactive Provider Assistance for P2P
... Up to 50-70% of Internet traffic is contributed by P2P applications Cache logic research: Internet protocol breakdown 1993 – 2006; Velocix: File-types on major P2P networks. ...
... Up to 50-70% of Internet traffic is contributed by P2P applications Cache logic research: Internet protocol breakdown 1993 – 2006; Velocix: File-types on major P2P networks. ...
home address
... Use IP in UDP tunnels. Use the source IP address and source port of Registration Request messages to locate the Mobile Node. Add an option to registration messages to inform of UDP ...
... Use IP in UDP tunnels. Use the source IP address and source port of Registration Request messages to locate the Mobile Node. Add an option to registration messages to inform of UDP ...
Performance Monitoring
... Several common metrics have been developed for measuring network performance. Some of the different ways in which network performance might be measured are as follows. Passive or active monitoring: - In passive monitoring the traffic at some point in the network is simply monitored. The pertinent fe ...
... Several common metrics have been developed for measuring network performance. Some of the different ways in which network performance might be measured are as follows. Passive or active monitoring: - In passive monitoring the traffic at some point in the network is simply monitored. The pertinent fe ...
CDW White Paper - WAN Optimization
... Sockets Layer (SSL) encryption as a default, even within enterprise networks. Security teams have been pushing for higher end-to-end security for decades, and application development and system performance are finally catching up. Encryption, however, comes with a downside: There’s no good way to op ...
... Sockets Layer (SSL) encryption as a default, even within enterprise networks. Security teams have been pushing for higher end-to-end security for decades, and application development and system performance are finally catching up. Encryption, however, comes with a downside: There’s no good way to op ...
Resume - OPResume.com
... Provided troubleshooting via telephone and in-person to 1550 internal and external customers, including the installation and configuration of software, password resets and first-line diagnosis/troubleshooting for computer hardware and software problems. Implemented an organization’s computer informa ...
... Provided troubleshooting via telephone and in-person to 1550 internal and external customers, including the installation and configuration of software, password resets and first-line diagnosis/troubleshooting for computer hardware and software problems. Implemented an organization’s computer informa ...
Internetworking
... Solution: protocol software running on each host and router smooths out the differences between the different networks. ...
... Solution: protocol software running on each host and router smooths out the differences between the different networks. ...
- Krest Technology
... In this Module, the diverse MT-IGP paths according to the link weights computed by OLWO. Monitored network and traffic data such as incoming traffic volume and link utilizations. At each short-time interval, ATC computes a new traffic splitting ratio across individual VRTs for re-assigning traffic i ...
... In this Module, the diverse MT-IGP paths according to the link weights computed by OLWO. Monitored network and traffic data such as incoming traffic volume and link utilizations. At each short-time interval, ATC computes a new traffic splitting ratio across individual VRTs for re-assigning traffic i ...
Lec_2
... needs of an organization and the type of technology used , a LAN can be as simple as two PCs and a printer in some one’s home office or it can extend through out a company and include voice ,sound ,and video peripherals .Currently ,LAN size is limited to a ...
... needs of an organization and the type of technology used , a LAN can be as simple as two PCs and a printer in some one’s home office or it can extend through out a company and include voice ,sound ,and video peripherals .Currently ,LAN size is limited to a ...
NETWORKING FUNDAMENTALS
... To allow multiple computers to communicate. Communication might be: • a download of an MP3 audio file for your MP3 player • checking the latest sports scores • using an instant-messaging service, such as Viber • sending text messages to a friend • writing an e-mail and sending it to a business assoc ...
... To allow multiple computers to communicate. Communication might be: • a download of an MP3 audio file for your MP3 player • checking the latest sports scores • using an instant-messaging service, such as Viber • sending text messages to a friend • writing an e-mail and sending it to a business assoc ...
Chapter 11
... TCP/IP Model of Layering • TCP/IP Layers – Network Interface - accepts IP datagrams and transmits them over a network (device driver or specific data link protocol) – Internet - routing and delivery of datagrams – Transport - provides communication from one application program on one machine to ano ...
... TCP/IP Model of Layering • TCP/IP Layers – Network Interface - accepts IP datagrams and transmits them over a network (device driver or specific data link protocol) – Internet - routing and delivery of datagrams – Transport - provides communication from one application program on one machine to ano ...
Part 1 R1 What is the difference between a host and an end system
... The types of application programs that run are web browser programs, web server programs, and e-mail readers and senders. So Yes a web server is an end system. R3 Why are standards important for protocols? ...
... The types of application programs that run are web browser programs, web server programs, and e-mail readers and senders. So Yes a web server is an end system. R3 Why are standards important for protocols? ...
Introduction to network management
... Software version information for the operating system, protocol software, or management software. Hardware version information for the interfaces or hardware controllers. Contact information indicating who to contact if problems with the device arise. Location information indicating the physical loc ...
... Software version information for the operating system, protocol software, or management software. Hardware version information for the interfaces or hardware controllers. Contact information indicating who to contact if problems with the device arise. Location information indicating the physical loc ...
Towards Software-Friendly Networks
... increase the richness of the API have not been very successful (e.g. RSVP [12]). While many applications could benefit from the QoS control RSVP offers, few applications find RSVP optimized for their needs. For example, Skype employs a number of its own proprietary tricks to figure out the current q ...
... increase the richness of the API have not been very successful (e.g. RSVP [12]). While many applications could benefit from the QoS control RSVP offers, few applications find RSVP optimized for their needs. For example, Skype employs a number of its own proprietary tricks to figure out the current q ...