Week-3
... VM software can run in kernel mode. The VMs should execute only in user mode Guest OSes also have user and kernel modes Virtual user mode – virtual kernel mode ...
... VM software can run in kernel mode. The VMs should execute only in user mode Guest OSes also have user and kernel modes Virtual user mode – virtual kernel mode ...
Threads - IFSC-USP
... implementation is up to development of the library. n Common in UNIX operating systems. ...
... implementation is up to development of the library. n Common in UNIX operating systems. ...
Java Threads
... implementation is up to development of the library. n Common in UNIX operating systems. ...
... implementation is up to development of the library. n Common in UNIX operating systems. ...
Chapter 1: Introduction to Operating Systems
... • Application base – Combination of hardware and operating system used to develop applications – Developers and users unwilling to abandon established ...
... • Application base – Combination of hardware and operating system used to develop applications – Developers and users unwilling to abandon established ...
2.01 - Avi Silberschatz's Home Page
... conclusion. It treats hardware and the operating system kernel as though they were all hardware. A virtual machine provides an interface identical to the underlying ...
... conclusion. It treats hardware and the operating system kernel as though they were all hardware. A virtual machine provides an interface identical to the underlying ...
A Survey of Contemporary Real-time Operating Systems
... sized to have the worst-case memory demand of the system. The low priority pool is given the remaining free memory. If the low priority tasks exhaust the low priority memory pool, they must wait for memory to be returned to the pool before further execution [1]. Dynamic memory management employs mem ...
... sized to have the worst-case memory demand of the system. The low priority pool is given the remaining free memory. If the low priority tasks exhaust the low priority memory pool, they must wait for memory to be returned to the pool before further execution [1]. Dynamic memory management employs mem ...
Silberschatz/7e Lecture Notes
... conclusion. It treats hardware and the operating system kernel as though they were all hardware A virtual machine provides an interface identical to the ...
... conclusion. It treats hardware and the operating system kernel as though they were all hardware A virtual machine provides an interface identical to the ...
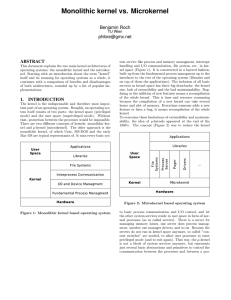
Monolithic kernel vs. Microkernel
... Exstensibility is the most prominent fact for µ-kernels. It is, beside its size, one of the biggest difference to monolithic kernels. Adding new features to a monolithic system means recompilation of the whole kernel, often including the whole driver infrastructure. If you have a new memeory managm ...
... Exstensibility is the most prominent fact for µ-kernels. It is, beside its size, one of the biggest difference to monolithic kernels. Adding new features to a monolithic system means recompilation of the whole kernel, often including the whole driver infrastructure. If you have a new memeory managm ...
High Performance Computing Prof. Matthew Jacob Department of Computer Science and Automation
... OpenSUSE, Ubuntu to Debian. So, these are all just not various of Linux, all of them will have the Linux kernel, there is only one Linux kernel, at any given point in time, of course,, they could be copies of older Linux kernels, but there is one most recent version of Linux, which would be the curr ...
... OpenSUSE, Ubuntu to Debian. So, these are all just not various of Linux, all of them will have the Linux kernel, there is only one Linux kernel, at any given point in time, of course,, they could be copies of older Linux kernels, but there is one most recent version of Linux, which would be the curr ...
pdf book chapter - LIRA-Lab
... alter the data of application B by simply accessing that part of main memory where that data are currently stored. Likewise, we need to ensure that applications can make use of facilities only as offered by the operating system. For instance, it should generally be prevented that an application can ...
... alter the data of application B by simply accessing that part of main memory where that data are currently stored. Likewise, we need to ensure that applications can make use of facilities only as offered by the operating system. For instance, it should generally be prevented that an application can ...
ch9
... Hole – variable size block of available memory new process is allocated memory from a hole Operating system maintains information about: a) allocated partitions b) free partitions (holes) ...
... Hole – variable size block of available memory new process is allocated memory from a hole Operating system maintains information about: a) allocated partitions b) free partitions (holes) ...
Operating Systems and Utility Programs
... Server portion resides on network server Client portion resides on each client computer ...
... Server portion resides on network server Client portion resides on each client computer ...
OS: Structures
... conclusion. It treats hardware and the operating system kernel as though they were all hardware A virtual machine provides an interface identical to the ...
... conclusion. It treats hardware and the operating system kernel as though they were all hardware A virtual machine provides an interface identical to the ...
Towards Trustworthy Virtualisation Environments: Xen Library OS
... provision of security services on top of the virtualisation layer. We consider these security services key in moving towards a fuller trustworthy virtualisation environment where the trust and security problems introduced by virtualised infrastructures can begin to be addressed [15]. In our view a t ...
... provision of security services on top of the virtualisation layer. We consider these security services key in moving towards a fuller trustworthy virtualisation environment where the trust and security problems introduced by virtualised infrastructures can begin to be addressed [15]. In our view a t ...
Catholic University College of Ghana Fiapre
... operating system. The development of networked computers that could be linked and communicate with each other, gave rise to distributed computing. ...
... operating system. The development of networked computers that could be linked and communicate with each other, gave rise to distributed computing. ...
Operating Systems and File Management 4 Operating System
... 4 File Management Metaphors Storage metaphors help you visualize and mentally organize the files on your disks and other storage devices ...
... 4 File Management Metaphors Storage metaphors help you visualize and mentally organize the files on your disks and other storage devices ...
ppt
... – Support binaries of all existing applications (no special system calls required) – No worse performance (but may be better) ...
... – Support binaries of all existing applications (no special system calls required) – No worse performance (but may be better) ...
SG9OS
... • Operating Systems for Personal Computers – Main goal was to make the operating system user friendly – The idea that revolutionized small computer operating systems was the BIOS (basic input-output operating system) > A chip that permitted a single operating system to function on different types of ...
... • Operating Systems for Personal Computers – Main goal was to make the operating system user friendly – The idea that revolutionized small computer operating systems was the BIOS (basic input-output operating system) > A chip that permitted a single operating system to function on different types of ...
Faithful Virtualization on a Real
... Virtualization is a term that is used in many different aspects of computer science and especially in the area of operating systems. In this paper we concentrate on virtual machines that enable running complete operating systems with all their applications on top of the host operating system [12]. W ...
... Virtualization is a term that is used in many different aspects of computer science and especially in the area of operating systems. In this paper we concentrate on virtual machines that enable running complete operating systems with all their applications on top of the host operating system [12]. W ...
Operating Systems: Processes and Threads Process model
... Library procedures May not be reentrant (second call to procedure before the first one is finished) Solution: rewrite the library or use an excluding jacket ...
... Library procedures May not be reentrant (second call to procedure before the first one is finished) Solution: rewrite the library or use an excluding jacket ...
Operating System Tutorial
... © Copyright 2016 by Tutorials Point (I) Pvt. Ltd. All the content and graphics published in this e-book are the property of Tutorials Point (I) Pvt. Ltd. The user of this e-book is prohibited to reuse, retain, copy, distribute or republish any contents or a part of contents of this e-book in any man ...
... © Copyright 2016 by Tutorials Point (I) Pvt. Ltd. All the content and graphics published in this e-book are the property of Tutorials Point (I) Pvt. Ltd. The user of this e-book is prohibited to reuse, retain, copy, distribute or republish any contents or a part of contents of this e-book in any man ...
"Virtual Machines: The State of the Art"
... We use the results of the Virtual machine monitor machines useful? comparison to determine Host operating system which techniques are Virtual machines have most suitable for which many practical uses in Hardware applications. We find many different kinds of that the new hardware environments. Physic ...
... We use the results of the Virtual machine monitor machines useful? comparison to determine Host operating system which techniques are Virtual machines have most suitable for which many practical uses in Hardware applications. We find many different kinds of that the new hardware environments. Physic ...
Semester 2 2012/2013
... sequence of instructions that execute for that process and this listing is referred to as a ________ of the process. ...
... sequence of instructions that execute for that process and this listing is referred to as a ________ of the process. ...
kubi-cs162f05lec01
... Nachos: Virtual OS Environment • You will be working with Nachos – Simulation environment – Hardware, interrupts, I/O – Execution of User Programs running on this platform ...
... Nachos: Virtual OS Environment • You will be working with Nachos – Simulation environment – Hardware, interrupts, I/O – Execution of User Programs running on this platform ...