3GPP TSG-SA1 #42 - 5G
... network functionalities and mobile edge computing (MEC) are the key tools of this applicationcentric networking. The goal of MEC is to bring cloud-computing capabilities, including computing and caching, at the edge of the mobile network, within the Radio Access Network (RAN), in close proximity to ...
... network functionalities and mobile edge computing (MEC) are the key tools of this applicationcentric networking. The goal of MEC is to bring cloud-computing capabilities, including computing and caching, at the edge of the mobile network, within the Radio Access Network (RAN), in close proximity to ...
Proxies, Active Networks, Re-configurable Terminals: The Cornerstones of Future Wireless Internet
... servers with the classical http protocol, but has to use a special translation server, instead. This allows to use a set of “lean“ protocols between the end-system and the translation server, in case of WAP optimised for usage on links with low bit rates, and thus well suited for today’s GSM wireles ...
... servers with the classical http protocol, but has to use a special translation server, instead. This allows to use a set of “lean“ protocols between the end-system and the translation server, in case of WAP optimised for usage on links with low bit rates, and thus well suited for today’s GSM wireles ...
Faculty of Computer Science & Engineering Chapter 04 .Wireless
... remote office building.Each sales person has both a PC and a laptop. The client wants to purchase a hardware solution that will permit each sales person to have wireless network connectivity for his or her PC and laptop. Only the PC or the laptop needs network access at any given time, and both have ...
... remote office building.Each sales person has both a PC and a laptop. The client wants to purchase a hardware solution that will permit each sales person to have wireless network connectivity for his or her PC and laptop. Only the PC or the laptop needs network access at any given time, and both have ...
Slides - TERENA Networking Conference 2010
... Physical Link Logical Link (may be a full physical link) ...
... Physical Link Logical Link (may be a full physical link) ...
Slides - TERENA Networking Conference 2008
... • Different stakeholders working together to provide a quality service • That reaches the users! • GÉANT2 is not just a backbone network! ...
... • Different stakeholders working together to provide a quality service • That reaches the users! • GÉANT2 is not just a backbone network! ...
Kaleidoscope 2009 - Powerpoint template for paper presentation
... sustainable competition environment to various participants in ecosystem of ICT by providing proper economic incentives ⑧ (Network Management) FNs should be able to operate, maintain and provision efficiently the increasing number of services and entities. ⑨ (Mobility) FNs should be designed and imp ...
... sustainable competition environment to various participants in ecosystem of ICT by providing proper economic incentives ⑧ (Network Management) FNs should be able to operate, maintain and provision efficiently the increasing number of services and entities. ⑨ (Mobility) FNs should be designed and imp ...
Week_Ten_Network_ppt
... CATV (originally "community antenna television," now often "community access television") is more commonly known as "cable TV." Television programs were brought to millions of people throughout the world who were connected to a community antenna, cable TV. Today, CATV has become an increasingly popu ...
... CATV (originally "community antenna television," now often "community access television") is more commonly known as "cable TV." Television programs were brought to millions of people throughout the world who were connected to a community antenna, cable TV. Today, CATV has become an increasingly popu ...
Peakflow® Solution
... and Management Peakflow is non-intrusive on the network. It leverages network telemetry (NetFlow, sFlow, etc.) provided by routers and switches to deliver pervasive network visibility without relying on costly inline probes or taps. Peakflow’s robust set of reports show network operators: • Where tr ...
... and Management Peakflow is non-intrusive on the network. It leverages network telemetry (NetFlow, sFlow, etc.) provided by routers and switches to deliver pervasive network visibility without relying on costly inline probes or taps. Peakflow’s robust set of reports show network operators: • Where tr ...
Public Network Principles
... Business e-mail with fairly large file attachments The base signal on a channel in the set of Digital Signal levels Mobile telephone for business and personal use ...
... Business e-mail with fairly large file attachments The base signal on a channel in the set of Digital Signal levels Mobile telephone for business and personal use ...
When WiMAX meets IMS TextStart WiMAX features wide coverage
... WiMAX features wide coverage, high bandwidth, easy deployment, and is applicable to fixed, roaming, and mobile scenarios. WiMAX is one of the best existing high-speed wireless broadband access technologies to cover areas not reached by wired broadband access, plus offers radio access bearers (RAB) f ...
... WiMAX features wide coverage, high bandwidth, easy deployment, and is applicable to fixed, roaming, and mobile scenarios. WiMAX is one of the best existing high-speed wireless broadband access technologies to cover areas not reached by wired broadband access, plus offers radio access bearers (RAB) f ...
Co-authors Point of View
... security issue: contents should be trusted independently from the location and the identity of who is providing them; mobility issue: avoiding service interruption when users move across different access networks; scalability issue: limited storage, bandwidth, and computational capabilities of servic ...
... security issue: contents should be trusted independently from the location and the identity of who is providing them; mobility issue: avoiding service interruption when users move across different access networks; scalability issue: limited storage, bandwidth, and computational capabilities of servic ...
GEYSERS_NCP_OGF28
... support for multiple switching technologies (MRN/MLN) PCE architecture and inter-PCE comms ...
... support for multiple switching technologies (MRN/MLN) PCE architecture and inter-PCE comms ...
FSP 150CC-T3204 - ADVA Optical Networking
... connection. It is ideal for applications such as mobile backhaul and enables the re-use of existing infrastructure that does not have Ethernet ports to deliver intelligent Carrier Ethernet 2.0 services. Support for both VCAT and LCAS encapsulation ensures interoperability with a wide range of indust ...
... connection. It is ideal for applications such as mobile backhaul and enables the re-use of existing infrastructure that does not have Ethernet ports to deliver intelligent Carrier Ethernet 2.0 services. Support for both VCAT and LCAS encapsulation ensures interoperability with a wide range of indust ...
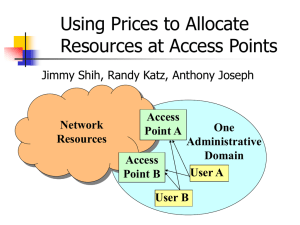
Design Review of Using Prices to Allocate Resources at a H
... telephones, and congestion prices for using their computers. Inform users the current connection qualities if they use their computers. When users use their telephone to make & receive calls, inform them how much cheaper it would be if they switch to their computers. ...
... telephones, and congestion prices for using their computers. Inform users the current connection qualities if they use their computers. When users use their telephone to make & receive calls, inform them how much cheaper it would be if they switch to their computers. ...
NANOG - Washington, DC, USA
... • SURFnet realised that a new infrastructure project was needed, but – the required funds couldn’t be delivered solely by the Ministry of Education, Culture and Science – the project would have a broader (economic) value – network and applications need to be developed simultaneously ...
... • SURFnet realised that a new infrastructure project was needed, but – the required funds couldn’t be delivered solely by the Ministry of Education, Culture and Science – the project would have a broader (economic) value – network and applications need to be developed simultaneously ...
webservice
... • Sender and receiver can be written in different programming language • Sender and receiver need not know what programming language the other part was written in Web services using SOAP ...
... • Sender and receiver can be written in different programming language • Sender and receiver need not know what programming language the other part was written in Web services using SOAP ...
Chapter 12 - YSU Computer Science & Information Systems
... • Allows you to configure multiple backup systems. – For example, you can configure an access server to consult a security server first and a local database second ...
... • Allows you to configure multiple backup systems. – For example, you can configure an access server to consult a security server first and a local database second ...
SANS Top 5 Essential Log Reports
... Clearly it is possible for a legitimate user to occasionally type in an incorrect password. If report information is provided in summary format, the amount of false positive “noise” should be minimal. The ability to pull additional authentication reports could also help an administrator clarify the ...
... Clearly it is possible for a legitimate user to occasionally type in an incorrect password. If report information is provided in summary format, the amount of false positive “noise” should be minimal. The ability to pull additional authentication reports could also help an administrator clarify the ...
TW-522 802.11ac Dual Radio Wallplate Specification Sheet
... beacon networks to deliver new services that take the customer experience to a new level, providing increased customer satisfaction and a competitive differentiator. ...
... beacon networks to deliver new services that take the customer experience to a new level, providing increased customer satisfaction and a competitive differentiator. ...
6. Next Generation Networks A. Transition to NGN B. Key
... A “call” in the next generation network can be viewed as a session in which the session establishes either a voice conversation or, ultimately, a multimedia (audio plus video) stream. There are two primary call control protocols unique to packet-based networks: H.323 SIP ...
... A “call” in the next generation network can be viewed as a session in which the session establishes either a voice conversation or, ultimately, a multimedia (audio plus video) stream. There are two primary call control protocols unique to packet-based networks: H.323 SIP ...
Oracle Internet Directory
... Oracle’s JAAS (Java Authentication and Authorization Services) implementation, plus ...
... Oracle’s JAAS (Java Authentication and Authorization Services) implementation, plus ...
01_423intro
... Rapidly developing Internet services set stringent requirements for network infrastructure & planning adaptivity service/system upgradability ...
... Rapidly developing Internet services set stringent requirements for network infrastructure & planning adaptivity service/system upgradability ...
The OBAN project and issues for standardisation
... This presentation introduces the concept of OBAN (Open Broadband Access Network), an European funded project under the IST 6th framework program. ...
... This presentation introduces the concept of OBAN (Open Broadband Access Network), an European funded project under the IST 6th framework program. ...