Lightpath Fragmentation for Efficient Spectrum
... its widespread use in wireless communications, OFDM has been recently introduced as a modulation format in optical communications [5]. Through optical OFDM, data belonging to a single traffic demand is split in multiple lower bit-rate sub-carriers, providing fine-granularity capacity to the connecti ...
... its widespread use in wireless communications, OFDM has been recently introduced as a modulation format in optical communications [5]. Through optical OFDM, data belonging to a single traffic demand is split in multiple lower bit-rate sub-carriers, providing fine-granularity capacity to the connecti ...
3rd Edition: Chapter 4
... They’re in PowerPoint form so you can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. In return for use, we only ask the following: If you use these slides (e.g., in a class) in substantially unaltered fo ...
... They’re in PowerPoint form so you can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. In return for use, we only ask the following: If you use these slides (e.g., in a class) in substantially unaltered fo ...
20111003-boyd-NDDI
... • Each individual node should function like an “exchange point” in terms of policy, cost, capabilities • Fully distributed exchange will operate as close to exchange point as possible given constraints: i.e. transport has additional associated costs – Inter-node transport scalability and funding nee ...
... • Each individual node should function like an “exchange point” in terms of policy, cost, capabilities • Fully distributed exchange will operate as close to exchange point as possible given constraints: i.e. transport has additional associated costs – Inter-node transport scalability and funding nee ...
No Slide Title - Virginia Tech
... • Dial-in modem pool with ~1,200 56K modems. • MSAP provides campus backbone access to local ISPs. – Ethernet in apartment complexes ...
... • Dial-in modem pool with ~1,200 56K modems. • MSAP provides campus backbone access to local ISPs. – Ethernet in apartment complexes ...
IPv4 and IPv6
... a) VER: IP version; 4 for IPv4 and 6 for IPv6 b) PRI: priority field defines priority of packets w.r.t. traffic congestion; 0-7: for packets that can slow down in event of congestion; 8-15 for real-time traffic with constant sending rate – Audio & Video. c) Flow label: (~ Service in IPv4) Special ha ...
... a) VER: IP version; 4 for IPv4 and 6 for IPv6 b) PRI: priority field defines priority of packets w.r.t. traffic congestion; 0-7: for packets that can slow down in event of congestion; 8-15 for real-time traffic with constant sending rate – Audio & Video. c) Flow label: (~ Service in IPv4) Special ha ...
IOSR Journal of Electronics and Communication Engineering (IOSR-JECE)
... GNS3 is an excellent complementary tool to real labs for network engineers, administrators and people want to study for certifications such as Cisco CCNA, CCNP, CCIP and CCIE as well as Juniper JNCIA, JNCIS and JNCIE.It can also be used to experiment features of Cisco IOS, Juniper JunOS or to check ...
... GNS3 is an excellent complementary tool to real labs for network engineers, administrators and people want to study for certifications such as Cisco CCNA, CCNP, CCIP and CCIE as well as Juniper JNCIA, JNCIS and JNCIE.It can also be used to experiment features of Cisco IOS, Juniper JunOS or to check ...
3rd Edition: Chapter 4
... They’re in PowerPoint form so you can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. In return for use, we only ask the following: If you use these slides (e.g., in a class) in substantially unaltered fo ...
... They’re in PowerPoint form so you can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. In return for use, we only ask the following: If you use these slides (e.g., in a class) in substantially unaltered fo ...
IMS_new_possibilities
... IMS Momentum The OMA (Open Mobile Alliance) “IMSinOMA” Requirements Document (RD) provides a single general use case which rationalizes IMS as the only globally standardized SIP-based architecture (to date) that addresses the needs of mobile operators in terms of session management, security, mob ...
... IMS Momentum The OMA (Open Mobile Alliance) “IMSinOMA” Requirements Document (RD) provides a single general use case which rationalizes IMS as the only globally standardized SIP-based architecture (to date) that addresses the needs of mobile operators in terms of session management, security, mob ...
Chapter 7 Lecture Presentation
... source and to any given destination Routing involves the selection of the path to be used to accomplish a given transfer Typically it is possible to attach a cost or distance to a link connecting two nodes Routing can then be posed as a shortest path ...
... source and to any given destination Routing involves the selection of the path to be used to accomplish a given transfer Typically it is possible to attach a cost or distance to a link connecting two nodes Routing can then be posed as a shortest path ...
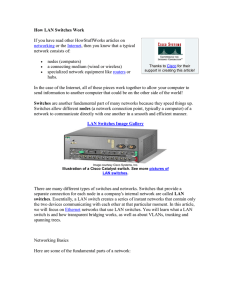
How LAN Switches Work
... You can see that a switch has the potential to radically change the way nodes communicate with each other. But you may be wondering what makes it different from a router. Switches usually work at Layer 2 (Data or Datalink) of the OSI Reference Model, using MAC addresses, while routers work at Layer ...
... You can see that a switch has the potential to radically change the way nodes communicate with each other. But you may be wondering what makes it different from a router. Switches usually work at Layer 2 (Data or Datalink) of the OSI Reference Model, using MAC addresses, while routers work at Layer ...
Internetworking, higher layer protocols TCP/IP and ATM Eytan Modiano Massachusetts Institute of Technology
... E.g., ATM (Asynchronous transfer mode) ...
... E.g., ATM (Asynchronous transfer mode) ...
TKN Performance Evaluation of a QoS-Aware Handover Mechanism S. Sroka and H. Karl
... hardware are easily and cheaply available from the mass market for data communication. However, it is not clear whether this IP-based protocol family will be able to fulfill all the requirements that are currently placed on mobile communication systems. In particular, current GSM-type solutions prov ...
... hardware are easily and cheaply available from the mass market for data communication. However, it is not clear whether this IP-based protocol family will be able to fulfill all the requirements that are currently placed on mobile communication systems. In particular, current GSM-type solutions prov ...
ppt
... receiver window size, Wm* , in segments, assuming a segment size of 1,460 bytes, for various types of networks. • As shown by the table, high-bandwidth, low-latency networks require large window sizes for the throughput of the TCP connection to use as much of the network bandwidth as possible. ...
... receiver window size, Wm* , in segments, assuming a segment size of 1,460 bytes, for various types of networks. • As shown by the table, high-bandwidth, low-latency networks require large window sizes for the throughput of the TCP connection to use as much of the network bandwidth as possible. ...
Dealing with multiple clients
... the center of large networks to a device that every twisted pair-based network with more than two machines had to use. The tree structure that resulted from this made Ethernet networks more reliable by preventing faults with (but not deliberate misbehavior of) one peer or its associated cable from a ...
... the center of large networks to a device that every twisted pair-based network with more than two machines had to use. The tree structure that resulted from this made Ethernet networks more reliable by preventing faults with (but not deliberate misbehavior of) one peer or its associated cable from a ...
3rd Edition: Chapter 4
... when looking for forwarding table entry for given destination address, use longest address prefix that matches destination address (more on this coming soon) Destination Address Range ...
... when looking for forwarding table entry for given destination address, use longest address prefix that matches destination address (more on this coming soon) Destination Address Range ...
Week_Eleven_ppt
... more different routes to the same destination from two different routing protocols. Administrative distance defines the reliability of a routing protocol. Each routing protocol is prioritized in order of most to least reliable (believable) using an administrative distance value. A lower numerical va ...
... more different routes to the same destination from two different routing protocols. Administrative distance defines the reliability of a routing protocol. Each routing protocol is prioritized in order of most to least reliable (believable) using an administrative distance value. A lower numerical va ...
eMerge Certification Module 1
... of the network. This IP Address can be setup to expire requiring the Host to get a new IP Address from the DHCP server. This method is used in both Public and Private networks. A Static IP Address is assigned by the Network Administrator. The Network Administrator will actually type in the IP Addres ...
... of the network. This IP Address can be setup to expire requiring the Host to get a new IP Address from the DHCP server. This method is used in both Public and Private networks. A Static IP Address is assigned by the Network Administrator. The Network Administrator will actually type in the IP Addres ...
MBone - UMBC
... know how to handle multicasting. Most routers are set up to move traditional IP unicast packets. Router manufacturers have been reluctant to create equipment that can do multicasting until there is a proven need for such equipment. But, as you might expect, it's difficult for users to try out a tech ...
... know how to handle multicasting. Most routers are set up to move traditional IP unicast packets. Router manufacturers have been reluctant to create equipment that can do multicasting until there is a proven need for such equipment. But, as you might expect, it's difficult for users to try out a tech ...
Introduction to the Internet, ping and traceroute
... • When you are looking at some site on the net, your computer and the one containing the site are hosts. • On the other hand, the computers that direct the traffic, for example your Internet service provider (ISP) are gateway/router ...
... • When you are looking at some site on the net, your computer and the one containing the site are hosts. • On the other hand, the computers that direct the traffic, for example your Internet service provider (ISP) are gateway/router ...
On the Accurate Identification of Network Service
... this paper, we introduce a new logarithm-based ranking scheme, which considers not only the correlation between related network flows, but also the implication of coincidental network traffic. As a result, this ranking scheme can rank dependency candidates more accurately and consistently. In other ...
... this paper, we introduce a new logarithm-based ranking scheme, which considers not only the correlation between related network flows, but also the implication of coincidental network traffic. As a result, this ranking scheme can rank dependency candidates more accurately and consistently. In other ...
Network Discovery Protocol LLDP and LLDPMED
... quality issues. VoIP, moreover, needs specific inventory management. Another challenge is that the protocol must allow IP telephony systems from different vendors to interoperate on one network. In April, 2006, the TIA (Telecommunications Industry Association) comes up with Link Layer Discovery Prot ...
... quality issues. VoIP, moreover, needs specific inventory management. Another challenge is that the protocol must allow IP telephony systems from different vendors to interoperate on one network. In April, 2006, the TIA (Telecommunications Industry Association) comes up with Link Layer Discovery Prot ...