
Connection con = DriverManager.getConnection( url, user, pass )
... • Unit of the Table, smallest unit in a relational database • For a table to be useful, it must enforce Entity Integrity. Entity Integrity—each row in a table can be located by using its Primary Key. 1st Law of Relational Databases Each row in a table must have an attribute(s) that uniquely locates ...
... • Unit of the Table, smallest unit in a relational database • For a table to be useful, it must enforce Entity Integrity. Entity Integrity—each row in a table can be located by using its Primary Key. 1st Law of Relational Databases Each row in a table must have an attribute(s) that uniquely locates ...
DBMS – SECURITY ISSUES
... The user account that owns the database and its tables, queries, forms, reports, and macros. Any user accounts that you add to the Admins group. In addition, you might want to add passwords to the accounts you create for users, or instruct users to add their own passwords. Users can create or change ...
... The user account that owns the database and its tables, queries, forms, reports, and macros. Any user accounts that you add to the Admins group. In addition, you might want to add passwords to the accounts you create for users, or instruct users to add their own passwords. Users can create or change ...
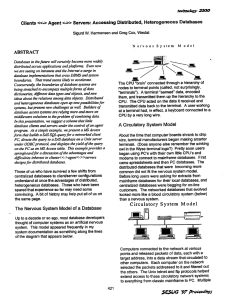
Clients <<-> Agent <->> Servers: Accessing Distributed, Heterogeneous Databases
... mechanism for managing update, insert, and delete transactions; a method for handling queries to more than one database and combining the answers; and, a method for using the edited results of one query as part of another query. Although these missing elements require some challenging technical work ...
... mechanism for managing update, insert, and delete transactions; a method for handling queries to more than one database and combining the answers; and, a method for using the edited results of one query as part of another query. Although these missing elements require some challenging technical work ...
Introduction to Database Systems
... Idea: If an action of Ti (say, writing X) affects Tj (which perhaps reads X), one of them, say Ti, will obtain the lock on X first and Tj is forced to wait until Ti completes; this effectively orders the transactions What if Tj already has a lock on Y and Ti later requests a lock on Y? (Deadlock!) T ...
... Idea: If an action of Ti (say, writing X) affects Tj (which perhaps reads X), one of them, say Ti, will obtain the lock on X first and Tj is forced to wait until Ti completes; this effectively orders the transactions What if Tj already has a lock on Y and Ti later requests a lock on Y? (Deadlock!) T ...
Introduction to SQL Server 2000
... track of the server installation as a whole and all other databases that are subsequently created. Although every database has a set of system catalogs that maintain information about objects it contains, the master database has system catalogs that keep information about disk space, file allocation ...
... track of the server installation as a whole and all other databases that are subsequently created. Although every database has a set of system catalogs that maintain information about objects it contains, the master database has system catalogs that keep information about disk space, file allocation ...
DATABASE TECHNOLOGY
... Data model? • Every DB has a data model which makes it possible to “hide” the physical representation of data. • A data model is a formalism that defines a notation for describing data on an abstract level together with a set of operations to manipulate data represented using this data model. • Data ...
... Data model? • Every DB has a data model which makes it possible to “hide” the physical representation of data. • A data model is a formalism that defines a notation for describing data on an abstract level together with a set of operations to manipulate data represented using this data model. • Data ...
Chapter 1: Introduction
... (called change or delta relations) and having a separate process that applies the changes over to a replica There are better ways of doing these now: Databases today provide built in materialized view facilities to automatically maintain summary data Databases provide built-in support for repl ...
... (called change or delta relations) and having a separate process that applies the changes over to a replica There are better ways of doing these now: Databases today provide built in materialized view facilities to automatically maintain summary data Databases provide built-in support for repl ...
Oracle Database 11g - Greater Cincinnati Oracle Users Group
... Faster performance for writes and copy operations May improve read performance Huge reduction in disk space usage • Great for document management, email archiving etc. ...
... Faster performance for writes and copy operations May improve read performance Huge reduction in disk space usage • Great for document management, email archiving etc. ...
data
... Failures may leave database in an inconsistent state with partial updates carried out Example: Transfer of funds (say $1000) from one account (say $5000) to another (say $2000) should either complete or not happen at all. ...
... Failures may leave database in an inconsistent state with partial updates carried out Example: Transfer of funds (say $1000) from one account (say $5000) to another (say $2000) should either complete or not happen at all. ...
Database
... If structure of a list is simple, i.e., one theme, no need to use database technology (video) ...
... If structure of a list is simple, i.e., one theme, no need to use database technology (video) ...
[Full Version] Lead2pass Latest Microsoft 70
... One of the databases on the virtual machine supports a highly active Online Transaction Processing (OLTP) application. Users report abnormally long wait times when they submit data in the application. Which two tools can you use to identify the longest running queries? Each correct answer presents a ...
... One of the databases on the virtual machine supports a highly active Online Transaction Processing (OLTP) application. Users report abnormally long wait times when they submit data in the application. Which two tools can you use to identify the longest running queries? Each correct answer presents a ...
Java Database Connectivity (JDBC)
... – For example, Open Database Connectivity (ODBC) was developed to create a single standard for database access in the Windows environment. ...
... – For example, Open Database Connectivity (ODBC) was developed to create a single standard for database access in the Windows environment. ...
Course Outline - U of L Class Index
... This book is more applied and should be more helpful in building your project. While Access is used in its examples, it is not designed to teach Access. Each team should purchase a book on Access as well. The recommended text is: Roger Jennings, Using Microsoft Access 2002 Special Edition, Que Books ...
... This book is more applied and should be more helpful in building your project. While Access is used in its examples, it is not designed to teach Access. Each team should purchase a book on Access as well. The recommended text is: Roger Jennings, Using Microsoft Access 2002 Special Edition, Que Books ...
Select - FSU Computer Science Department
... Customer c= customer.read(); rental.reset(); while (not rental.eof()) { Rental r[] = rental.readByAcctId(c.accountId); for (int i=0; i
... Customer c= customer.read(); rental.reset(); while (not rental.eof()) { Rental r[] = rental.readByAcctId(c.accountId); for (int i=0; i
Web Spatial Database Development and Programming
... database and programming training process including database design and manipulation, computer programming, programming syntax, data types, data structure, control structures, and an integrated programming environment (such as Eclipse and Tomcat) will be introduced and practiced during the lectures ...
... database and programming training process including database design and manipulation, computer programming, programming syntax, data types, data structure, control structures, and an integrated programming environment (such as Eclipse and Tomcat) will be introduced and practiced during the lectures ...
Entities and Attributes
... The great thing is relational databases aren't new. They've been around since the '70s. So you're coming in at a time when the methods for modeling a database have been battle tested over four decades. We know what works and what doesn't. And to design a good database, a large part of it is just to ...
... The great thing is relational databases aren't new. They've been around since the '70s. So you're coming in at a time when the methods for modeling a database have been battle tested over four decades. We know what works and what doesn't. And to design a good database, a large part of it is just to ...
Schwab PowerPoint template
... Can save the connections (structure attributes) to the objects and re-open them Has attributes such as read-only to allow multiple user to access the same data objects. ...
... Can save the connections (structure attributes) to the objects and re-open them Has attributes such as read-only to allow multiple user to access the same data objects. ...
Spatial databases 5
... structure on the part of the user e.g. user may need to be aware that polygons are composed of arcs, and stored as arc records, cannot treat them simply as objects and let the system take care of the internal structure users are required to have too much knowledge of the database model, cannot c ...
... structure on the part of the user e.g. user may need to be aware that polygons are composed of arcs, and stored as arc records, cannot treat them simply as objects and let the system take care of the internal structure users are required to have too much knowledge of the database model, cannot c ...
CUSTOMER_CODE SMUDE DIVISION_CODE SMUDE
... memory. External sorting algorithms are more device dependent than internal sorting. External Merge Sort is a relatively common used algorithm, based on the internal sorting and external merging principle. In general, this strategy is called Divide and Conquer : 1. Divide the data into parts that ar ...
... memory. External sorting algorithms are more device dependent than internal sorting. External Merge Sort is a relatively common used algorithm, based on the internal sorting and external merging principle. In general, this strategy is called Divide and Conquer : 1. Divide the data into parts that ar ...
slides - Jim Paterson
... This is the language which is used to define queries A query is a request to a DBMS for some specific information Relational databases are sometimes referred to as SQL databases Introduction to Database Development ...
... This is the language which is used to define queries A query is a request to a DBMS for some specific information Relational databases are sometimes referred to as SQL databases Introduction to Database Development ...
Microsoft Jet Database Engine
The Microsoft Jet Database Engine is a database engine on which several Microsoft products have been built. A database engine is the underlying component of a database, a collection of information stored on a computer in a systematic way. The first version of Jet was developed in 1992, consisting of three modules which could be used to manipulate a database.Database connect for MicrosoftJET stands for Joint Engine Technology, sometimes being referred to as Microsoft JET Engine or simply Jet. Microsoft Access and Visual Basic use or have used Jet as their underlying database engine. It has since been superseded for general use, however, first by Microsoft Desktop Engine (MSDE), then later by SQL Server Express. For larger database needs, Jet databases can be upgraded (or, in Microsoft parlance, ""up-sized"") to Microsoft's flagship database product, SQL Server.However, this does not mean that a MS Jet (Red) database cannot match MS SQL Server in storage capacity. A 5 billion record MS Jet (Red) database with compression and encryption turned on requires about 1 terabyte of disk storage space, comprising hundreds of (*.mdb) files, each acting as partial table, and not as a database in itself.Over the years, Jet has become almost synonymous with Microsoft Access, to the extent that many people refer to a Jet database as an ""Access database"".










![[Full Version] Lead2pass Latest Microsoft 70](http://s1.studyres.com/store/data/000506143_1-f39b1c7b66032d3919d6b0d8b8776e0e-300x300.png)











