Report of the Task Force to Investigate an E
... IV. Get feedback from departments and WG's. Chisman met with the Humanities/Social Science public service librarians on Thursday, November 29 to review the workflow and journal use study data elements and to answer questions. One of the main concerns is with the staffing required for this database. ...
... IV. Get feedback from departments and WG's. Chisman met with the Humanities/Social Science public service librarians on Thursday, November 29 to review the workflow and journal use study data elements and to answer questions. One of the main concerns is with the staffing required for this database. ...
MCS21416 - File Storage
... – times during the day/week when there will be a high demand made on the database (called the peak load). ...
... – times during the day/week when there will be a high demand made on the database (called the peak load). ...
transparently - Indico
... Connect to oracle:://oradb/oraschema, authenticate, start the monitoring and give me a ...
... Connect to oracle:://oradb/oraschema, authenticate, start the monitoring and give me a ...
Client/Server and Middleware
... logic, data processing logic and some business rules logic (frontend programs) Database server performs all data storage and access processing (back-end functions) – DBMS is only on server Advantages include:Clients do not have to be as powerful, only the database server requires processing powe ...
... logic, data processing logic and some business rules logic (frontend programs) Database server performs all data storage and access processing (back-end functions) – DBMS is only on server Advantages include:Clients do not have to be as powerful, only the database server requires processing powe ...
Client/Server and Middleware
... logic, data processing logic and some business rules logic (frontend programs) Database server performs all data storage and access processing (back-end functions) – DBMS is only on server Advantages include:Clients do not have to be as powerful, only the database server requires processing powe ...
... logic, data processing logic and some business rules logic (frontend programs) Database server performs all data storage and access processing (back-end functions) – DBMS is only on server Advantages include:Clients do not have to be as powerful, only the database server requires processing powe ...
Dealing with threats to databases
... Granular access control Limit application access Implement fine grained access control (row level access, table level access) Make sure database control is at database layer and not application layer ...
... Granular access control Limit application access Implement fine grained access control (row level access, table level access) Make sure database control is at database layer and not application layer ...
Chapter 1
... to add a component in the middle - create a three-tier system - For Web-based database access, the middle tier can run applications (client just gets results) DB Client ...
... to add a component in the middle - create a three-tier system - For Web-based database access, the middle tier can run applications (client just gets results) DB Client ...
“Oracle Database 11g: SQL Tuning Workshop”
... Gain expertise in relational database data management as you learn how to effectively use SQL commands against your business data. These features will help you query and manipulate data within the database, use the dictionary views to retrieve metadata and create reports about their schema objects. ...
... Gain expertise in relational database data management as you learn how to effectively use SQL commands against your business data. These features will help you query and manipulate data within the database, use the dictionary views to retrieve metadata and create reports about their schema objects. ...
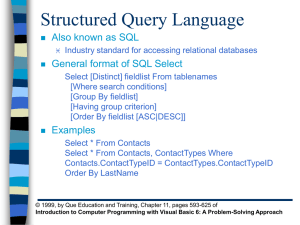
Query / Restrict Operations with Relational Tables
... •(D OR E) AND F may not be the same as D OR (E AND F) •NOT (A and B) may not be the same as [ NOT (A) AND NOT (B)] •Typically need to clarify order with delimiters ...
... •(D OR E) AND F may not be the same as D OR (E AND F) •NOT (A and B) may not be the same as [ NOT (A) AND NOT (B)] •Typically need to clarify order with delimiters ...
Database Security - People
... These are another source of passwords. When we select the location to save the Data Transformation Package, it can be seen in the SQL Profiler that msdb.dbo.sp_add_dtspackage is used to save the data (including the connection passwords) in msdb.dbo.sysdtspackages system table. Nevertheless, users in ...
... These are another source of passwords. When we select the location to save the Data Transformation Package, it can be seen in the SQL Profiler that msdb.dbo.sp_add_dtspackage is used to save the data (including the connection passwords) in msdb.dbo.sysdtspackages system table. Nevertheless, users in ...
Click install Installation Oracle 11g Express
... To unlock the HR user so you can experiment with it, do the following: Open SQL*Developer and open the connection for system-xe that we created in the last section. After the SQL Worksheet displays, type command ...
... To unlock the HR user so you can experiment with it, do the following: Open SQL*Developer and open the connection for system-xe that we created in the last section. After the SQL Worksheet displays, type command ...
DATABASE MANAGEMENT SYSTEM
... store data. The tables of records can be connected by common key values. While working for IBM, E.F. Codd designed this structure in 1972.The model is not easy for the end user to run queries with because it may require a complex combination of many ...
... store data. The tables of records can be connected by common key values. While working for IBM, E.F. Codd designed this structure in 1972.The model is not easy for the end user to run queries with because it may require a complex combination of many ...
BANKS: Browsing and Keyword Searching in Relational Databases
... results with the function log(1 + x), where x is the in-degree. Our use of logarithms in edge and node weights is similar to term weighting schemes in information retrieval. Node weights and tree weights are combined to get an overall relevance score. We experimented with additive and multiplicative ...
... results with the function log(1 + x), where x is the in-degree. Our use of logarithms in edge and node weights is similar to term weighting schemes in information retrieval. Node weights and tree weights are combined to get an overall relevance score. We experimented with additive and multiplicative ...
Lecture 2
... database_name – it represents the name of a new database. ON – it lets to explicitly define database files. PRIMARY – it indicates that the first file presented in files_defintion becomes the primary data file. LOG ON – it lets to explicitly define log files. file_definition – it specifies list of f ...
... database_name – it represents the name of a new database. ON – it lets to explicitly define database files. PRIMARY – it indicates that the first file presented in files_defintion becomes the primary data file. LOG ON – it lets to explicitly define log files. file_definition – it specifies list of f ...
Concurrency control - OOP January Trimester 2011
... – Concurrency control concepts • Motivation • If we insist only one transaction can execute at a time, in serial order, then performance will be quite poor. • Concurrency Control is a method for controlling or scheduling the operations of transactions in such a way that concurrent transactions can b ...
... – Concurrency control concepts • Motivation • If we insist only one transaction can execute at a time, in serial order, then performance will be quite poor. • Concurrency Control is a method for controlling or scheduling the operations of transactions in such a way that concurrent transactions can b ...
Main Responsibilities
... The work is delivered to a high level of accuracy and within team Service Level Agreements. That there is clear communication back to the campaign manager to minimise problems and maximise opportunities in data selection. There is a systematic and planned approach to managing every selection a ...
... The work is delivered to a high level of accuracy and within team Service Level Agreements. That there is clear communication back to the campaign manager to minimise problems and maximise opportunities in data selection. There is a systematic and planned approach to managing every selection a ...
Table 2.1 Simple Visual Basic Data Types
... Uses Jet DB engine to access databases Used when developing client/server application that access remote ODBC database system Requires Enterprise edition of VB & 32-bit OS ...
... Uses Jet DB engine to access databases Used when developing client/server application that access remote ODBC database system Requires Enterprise edition of VB & 32-bit OS ...
Distributed Databases - Computer Science, Stony Brook University
... – If no data is stored at headquarters, the monthly mailing requires that 100,000 rows be transmitted in a single day, which might clog the network – If we replicate, the time to register a new customer might suffer because of the remote update • But this update can be done by a separate transaction ...
... – If no data is stored at headquarters, the monthly mailing requires that 100,000 rows be transmitted in a single day, which might clog the network – If we replicate, the time to register a new customer might suffer because of the remote update • But this update can be done by a separate transaction ...
Insert Picture Here
... Multiple platform support Multiple database support Increases migration productivity Read only visualization of database data models ...
... Multiple platform support Multiple database support Increases migration productivity Read only visualization of database data models ...
Lab5
... • postmaster is the PostgreSQL multiuser database server. • In order for a client application to access a database it connects to a running postmaster. • The postmaster then starts a separate server process postgres to handle the connection. • The postmaster also manages the communication among ...
... • postmaster is the PostgreSQL multiuser database server. • In order for a client application to access a database it connects to a running postmaster. • The postmaster then starts a separate server process postgres to handle the connection. • The postmaster also manages the communication among ...
The Relational versus Hierarchical Database Debate Continues
... In a relational or hierarchical database, the software allows you to organize and access data in a manner suited to your needs withoul having to be concerned with the physical storage of the data. The physical and logical structures are independent. However, the software uses both structures to stor ...
... In a relational or hierarchical database, the software allows you to organize and access data in a manner suited to your needs withoul having to be concerned with the physical storage of the data. The physical and logical structures are independent. However, the software uses both structures to stor ...
Microsoft Jet Database Engine
The Microsoft Jet Database Engine is a database engine on which several Microsoft products have been built. A database engine is the underlying component of a database, a collection of information stored on a computer in a systematic way. The first version of Jet was developed in 1992, consisting of three modules which could be used to manipulate a database.Database connect for MicrosoftJET stands for Joint Engine Technology, sometimes being referred to as Microsoft JET Engine or simply Jet. Microsoft Access and Visual Basic use or have used Jet as their underlying database engine. It has since been superseded for general use, however, first by Microsoft Desktop Engine (MSDE), then later by SQL Server Express. For larger database needs, Jet databases can be upgraded (or, in Microsoft parlance, ""up-sized"") to Microsoft's flagship database product, SQL Server.However, this does not mean that a MS Jet (Red) database cannot match MS SQL Server in storage capacity. A 5 billion record MS Jet (Red) database with compression and encryption turned on requires about 1 terabyte of disk storage space, comprising hundreds of (*.mdb) files, each acting as partial table, and not as a database in itself.Over the years, Jet has become almost synonymous with Microsoft Access, to the extent that many people refer to a Jet database as an ""Access database"".