Insert, Update and Delete in Access
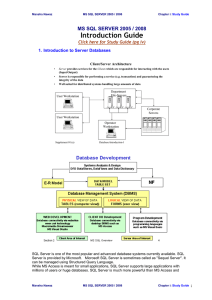
... All advanced database management systems include some kind of service applications as part of the database system. For example, to use the SQL Server database, you must have an application called "SQL Server Engine" running on the computer. This application is a windows service (a hidden application ...
... All advanced database management systems include some kind of service applications as part of the database system. For example, to use the SQL Server database, you must have an application called "SQL Server Engine" running on the computer. This application is a windows service (a hidden application ...
Fragmentation - UK SQL Server User Group
... Recommend higher cluster sizes as SQL Server deals with 8K pages and 64K extents – use a cluster size of 4K so you can defrag (/A option of FORMAT) On fresh NTFS volume, Master File Table and a number of system logs are held near middle of the new volume (prevents ...
... Recommend higher cluster sizes as SQL Server deals with 8K pages and 64K extents – use a cluster size of 4K so you can defrag (/A option of FORMAT) On fresh NTFS volume, Master File Table and a number of system logs are held near middle of the new volume (prevents ...
ppt
... evaluating a query can be enormous • Example: performing a r X s followed by a selection r.A = s.B is much slower than performing a join on the same condition • Need to estimate the cost of operations • Depends critically on statistical information about relations which the database must maintain • ...
... evaluating a query can be enormous • Example: performing a r X s followed by a selection r.A = s.B is much slower than performing a join on the same condition • Need to estimate the cost of operations • Depends critically on statistical information about relations which the database must maintain • ...
A Real World Scenario of a SQL Server 2005 Database
... Related information was successfully captured via the customized Windows Forensic Tool chest tool executed during the verification stage of this investigation. ...
... Related information was successfully captured via the customized Windows Forensic Tool chest tool executed during the verification stage of this investigation. ...
Role
... Changes made to a profile via ALTER PROFILE command take effect for subsequent sessions only. A profile that has users assigned to it can be dropped only via the command DROP PROFILE profile CASCADE. In that case, Oracle assigns the DEFAULT profile to all users who had the dropped profile as their ...
... Changes made to a profile via ALTER PROFILE command take effect for subsequent sessions only. A profile that has users assigned to it can be dropped only via the command DROP PROFILE profile CASCADE. In that case, Oracle assigns the DEFAULT profile to all users who had the dropped profile as their ...
Final Exam Review
... d. interval day to second 8. To remove all the rows from the table without generating “undo” or “rollback” we should use the command: a. drop rows b. delete rows c. delete table d. truncate table 9. Comments on tables and columns can be stored for documentation by: a. embedding /* comment */ within ...
... d. interval day to second 8. To remove all the rows from the table without generating “undo” or “rollback” we should use the command: a. drop rows b. delete rows c. delete table d. truncate table 9. Comments on tables and columns can be stored for documentation by: a. embedding /* comment */ within ...
Alarm Server
... OEGraphics View, Notes View) have what is known as three-tier Client-Server architecture. Each of the components listed above is a Client, which uses one or more Server components to provide them with the data that they request. This data is then displayed by the Client to the user. In turn, the Ser ...
... OEGraphics View, Notes View) have what is known as three-tier Client-Server architecture. Each of the components listed above is a Client, which uses one or more Server components to provide them with the data that they request. This data is then displayed by the Client to the user. In turn, the Ser ...
Distributed Database Systems
... waiting for the response, holds on to other locks! – If sites or links fail, Xact cannot commit until they are back up. – Even if there is no failure, committing must follow an expensive commit protocol with many msgs. ...
... waiting for the response, holds on to other locks! – If sites or links fail, Xact cannot commit until they are back up. – Even if there is no failure, committing must follow an expensive commit protocol with many msgs. ...
Distributed Databases
... – Sends lock requests to remote sites, and while waiting for the response, holds on to other locks! – If sites or links fail, Xact cannot commit until they are back up. – Even if there is no failure, committing must follow an expensive commit protocol with many msgs. ...
... – Sends lock requests to remote sites, and while waiting for the response, holds on to other locks! – If sites or links fail, Xact cannot commit until they are back up. – Even if there is no failure, committing must follow an expensive commit protocol with many msgs. ...
Triggers - Department Of Computing
... Whenever some details for an employee are deleted or updated, both the previous and new details are recorded in an audit table to allow tracing the history of changes. An insert operation cannot be recorded with this trigger as old.empno has no value. ...
... Whenever some details for an employee are deleted or updated, both the previous and new details are recorded in an audit table to allow tracing the history of changes. An insert operation cannot be recorded with this trigger as old.empno has no value. ...
Introduction to Web Development
... table’s structure, use the mysqli_info() function to return information about the query The mysqli_info() function returns the number of operations for various types of actions, depending on the type of query The mysqli_info() function returns information about the last query that was executed on th ...
... table’s structure, use the mysqli_info() function to return information about the query The mysqli_info() function returns the number of operations for various types of actions, depending on the type of query The mysqli_info() function returns information about the last query that was executed on th ...
Slides
... – Sends lock requests to remote sites, and while waiting for the response, holds on to other locks! – If sites or links fail, Xact cannot commit until they are back up. – Even if there is no failure, committing must follow an expensive commit protocol with many msgs. ...
... – Sends lock requests to remote sites, and while waiting for the response, holds on to other locks! – If sites or links fail, Xact cannot commit until they are back up. – Even if there is no failure, committing must follow an expensive commit protocol with many msgs. ...
Lecture 5 (SQL data definition)
... • Originally ‘Sequel’ Structured English query Language, part of an IBM project in the 70’s • Sequel was already taken, so it became SQL - Structured Query Language ...
... • Originally ‘Sequel’ Structured English query Language, part of an IBM project in the 70’s • Sequel was already taken, so it became SQL - Structured Query Language ...
Chapter # 8 (Advanced SQL)
... Implicit cursor: automatically created when SQL returns only one value Explicit cursor: holds the output of an SQL statement that may return two or more rows Cursor-style processor retrieves data from cursor one row at a time Current row copied to PL/SQL variables ...
... Implicit cursor: automatically created when SQL returns only one value Explicit cursor: holds the output of an SQL statement that may return two or more rows Cursor-style processor retrieves data from cursor one row at a time Current row copied to PL/SQL variables ...
Lecture 5: Active Databases
... Whenever some details for an employee are deleted or updated, both the previous and new details are recorded in an audit table to allow tracing the history of changes. An insert operation cannot be recorded with this trigger as old.empno has no value. ...
... Whenever some details for an employee are deleted or updated, both the previous and new details are recorded in an audit table to allow tracing the history of changes. An insert operation cannot be recorded with this trigger as old.empno has no value. ...
Solutions for the Object-Relational Databases Design
... systems, we conclude that, if using objectrelational databases, it is appropriate to choose any of them based on the existing system characteristics. A top-down approach is appropriate and desirable in a situation where there is not implemented an informatics system or if there are disparate applica ...
... systems, we conclude that, if using objectrelational databases, it is appropriate to choose any of them based on the existing system characteristics. A top-down approach is appropriate and desirable in a situation where there is not implemented an informatics system or if there are disparate applica ...
Sliding-Window Filtering: An Efficient Algorithm for Incremental Mining
... overhead due to the need of keeping a portion of database in memory, as indicated in [13], could become more severe in the presence of a large database upon which an incremental mining process is usually performed. To the best of our knowledge, there is little progress made thus far to explicitly ad ...
... overhead due to the need of keeping a portion of database in memory, as indicated in [13], could become more severe in the presence of a large database upon which an incremental mining process is usually performed. To the best of our knowledge, there is little progress made thus far to explicitly ad ...
Hibernate
... Some jar files that are here may not be required for your particular version of Hibernate Or you may need some other jar files. To make sure that you have the right set of libraries, always check the README.txt in the Hibernate distribution package. This contains an up to date list of all required a ...
... Some jar files that are here may not be required for your particular version of Hibernate Or you may need some other jar files. To make sure that you have the right set of libraries, always check the README.txt in the Hibernate distribution package. This contains an up to date list of all required a ...
Automating layout of relational databases
... that involves the scan of a large table (or index), it may be advantageous to define a layout in which the referenced table (or index) is allocated on a large number of disks. This is because the object can be scanned in parallel on all disks, thereby reducing the I/O response time for that query. O ...
... that involves the scan of a large table (or index), it may be advantageous to define a layout in which the referenced table (or index) is allocated on a large number of disks. This is because the object can be scanned in parallel on all disks, thereby reducing the I/O response time for that query. O ...
1411_Lecture3
... A language called Structured Query Language (SQL) is an international standard used with relational databases to perform queries (that is, to request information that satisfies given criteria) and to manipulate data. ...
... A language called Structured Query Language (SQL) is an international standard used with relational databases to perform queries (that is, to request information that satisfies given criteria) and to manipulate data. ...
SQL Object Level Recovery Native
... backup you are restoring from and the database you are restoring to. SQL Object Level Recovery Native + SQL Compare Pro + SQL Data Compare Pro + SQL Dependency Tracker + SQL Packager + SQL Prompt Pro + SQL Refactor + SQL Backup Pro + SQL Data Generator + SQL Multi Script + SQL Doc + SQL Comparison S ...
... backup you are restoring from and the database you are restoring to. SQL Object Level Recovery Native + SQL Compare Pro + SQL Data Compare Pro + SQL Dependency Tracker + SQL Packager + SQL Prompt Pro + SQL Refactor + SQL Backup Pro + SQL Data Generator + SQL Multi Script + SQL Doc + SQL Comparison S ...
Abstract Factory DAAB
... data access independent of the ADO.NET provider. The DAAB is a great tool that allows very easy access to the Sql Server ADO.NET driver using single line methods for example ExecuteDataset, ExecuteReader, etc. The problem behind this implementation is that every method was implemented as a static me ...
... data access independent of the ADO.NET provider. The DAAB is a great tool that allows very easy access to the Sql Server ADO.NET driver using single line methods for example ExecuteDataset, ExecuteReader, etc. The problem behind this implementation is that every method was implemented as a static me ...
JDBC - SoftUni
... JDBC Components The JDBC API provides the following interfaces and classes: DriverManager – This class manages a list of database drivers. Driver – This interface handles the communications with the database server. Connection – The connection object represents communication context. Stat ...
... JDBC Components The JDBC API provides the following interfaces and classes: DriverManager – This class manages a list of database drivers. Driver – This interface handles the communications with the database server. Connection – The connection object represents communication context. Stat ...
Microsoft Jet Database Engine
The Microsoft Jet Database Engine is a database engine on which several Microsoft products have been built. A database engine is the underlying component of a database, a collection of information stored on a computer in a systematic way. The first version of Jet was developed in 1992, consisting of three modules which could be used to manipulate a database.Database connect for MicrosoftJET stands for Joint Engine Technology, sometimes being referred to as Microsoft JET Engine or simply Jet. Microsoft Access and Visual Basic use or have used Jet as their underlying database engine. It has since been superseded for general use, however, first by Microsoft Desktop Engine (MSDE), then later by SQL Server Express. For larger database needs, Jet databases can be upgraded (or, in Microsoft parlance, ""up-sized"") to Microsoft's flagship database product, SQL Server.However, this does not mean that a MS Jet (Red) database cannot match MS SQL Server in storage capacity. A 5 billion record MS Jet (Red) database with compression and encryption turned on requires about 1 terabyte of disk storage space, comprising hundreds of (*.mdb) files, each acting as partial table, and not as a database in itself.Over the years, Jet has become almost synonymous with Microsoft Access, to the extent that many people refer to a Jet database as an ""Access database"".