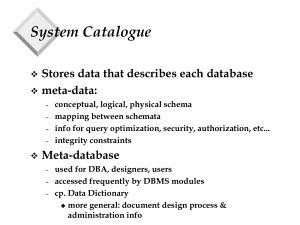
Installation and setup
... Installation and setup Most of the off-the-shelf products these days come with an installer. These installation programs, besides copying files into the target folder also copy DLLs and OCXs into your Windows/System32 folder and change your system configuration. If these DLLs are ActiveX controls, t ...
... Installation and setup Most of the off-the-shelf products these days come with an installer. These installation programs, besides copying files into the target folder also copy DLLs and OCXs into your Windows/System32 folder and change your system configuration. If these DLLs are ActiveX controls, t ...
oodbs - COW :: Ceng
... • Some objects in the host program are persistent. Changing such objects (through an assignment to an instance variable or with a method application) directly and transparently affects the corresponding database object • Accessing an object using its oid causes an “object fault” similar to pagefault ...
... • Some objects in the host program are persistent. Changing such objects (through an assignment to an instance variable or with a method application) directly and transparently affects the corresponding database object • Accessing an object using its oid causes an “object fault” similar to pagefault ...
Query-aware Test Generation Using a Relational Constraint Solver
... executing these queries might not return meaningful results. Recent approaches introduced query-aware database generation [2], [3]. These approaches use the information from the queries to constrain the data generator to generate databases that provide interesting results upon query executions. Quer ...
... executing these queries might not return meaningful results. Recent approaches introduced query-aware database generation [2], [3]. These approaches use the information from the queries to constrain the data generator to generate databases that provide interesting results upon query executions. Quer ...
Slides - Duke CS
... Statistical Inference And Learning The final step performs marginal inference on the factor graph variables to learn the probabilities of different values. The inference step we take the grounded graph (i.e., the five files written during the grounding step) as input, and a number of arguments to s ...
... Statistical Inference And Learning The final step performs marginal inference on the factor graph variables to learn the probabilities of different values. The inference step we take the grounded graph (i.e., the five files written during the grounding step) as input, and a number of arguments to s ...
pkirs.utep.edu
... Computer support specialists provide help and advice to people and organizations using computer software or equipment. Some, called technical support specialists, support information technology (IT) Computer Support Specialists employees within their organization. Others, called help-desk technician ...
... Computer support specialists provide help and advice to people and organizations using computer software or equipment. Some, called technical support specialists, support information technology (IT) Computer Support Specialists employees within their organization. Others, called help-desk technician ...
SQL Server 2000 OLTP best practices
... SQL Server 2005 OLTP Implementation findings: SQL Server 2005 can use more CPU In-place application upgrades from SS2K to SS2K5 (same hardware) often result in 20-30% more CPU utilization Especially noticeable with batch or serialized operations The problem is primarily attributed to: Higher query ...
... SQL Server 2005 OLTP Implementation findings: SQL Server 2005 can use more CPU In-place application upgrades from SS2K to SS2K5 (same hardware) often result in 20-30% more CPU utilization Especially noticeable with batch or serialized operations The problem is primarily attributed to: Higher query ...
Simple and practical techniques to manage small databases,
... not a portable database, but rather a serverbased database. For these reasons, two extra files with the basic information attached, i.e., a Microsoft® Excel® file and an Access® file (which can also be read with LibreOffice Calc and Base, respectively), were made available for download. Both files, ...
... not a portable database, but rather a serverbased database. For these reasons, two extra files with the basic information attached, i.e., a Microsoft® Excel® file and an Access® file (which can also be read with LibreOffice Calc and Base, respectively), were made available for download. Both files, ...
Preventing Transaction Logs From Filling Up
... growing too large. This document will cover the steps necessary to recover in the event that the transaction log has grown too large, manual truncation of the transaction log before it becomes a problem and how to schedule a maintenance plan. The transaction log is responsible for keeping track of a ...
... growing too large. This document will cover the steps necessary to recover in the event that the transaction log has grown too large, manual truncation of the transaction log before it becomes a problem and how to schedule a maintenance plan. The transaction log is responsible for keeping track of a ...
Introduction to Database Systems, Data Modeling and SQL
... Logical Data Model • Translation of the conceptual model into structures that can be implemented using a DBMS. This usually means the models specifies tables and columns. ...
... Logical Data Model • Translation of the conceptual model into structures that can be implemented using a DBMS. This usually means the models specifies tables and columns. ...
Oracle database concepts A database schema is a logical container
... dictionary tables and views for a database are stored in the SYSTEM tablespace. Because the SYSTEM tablespace is always online when the database is open, the data dictionary is always available when the database is open. The Oracle Database user SYS owns all base tables and user-accessible views of ...
... dictionary tables and views for a database are stored in the SYSTEM tablespace. Because the SYSTEM tablespace is always online when the database is open, the data dictionary is always available when the database is open. The Oracle Database user SYS owns all base tables and user-accessible views of ...
notes #15
... • Provides two methods for securing a database: – setting a password for opening a database (system security); – user-level security, which can be used to limit the parts of the database that a user can read or update (data security). ...
... • Provides two methods for securing a database: – setting a password for opening a database (system security); – user-level security, which can be used to limit the parts of the database that a user can read or update (data security). ...
chays.frankl.issta00.pdf
... space I to an output space O. Its speci cation can be expressed as a function (or, more generally, a relation) from I to O. Thus, we can test a database application by selecting values from I , executing the application on them, and checking whether the resulting values from O agree with the speci c ...
... space I to an output space O. Its speci cation can be expressed as a function (or, more generally, a relation) from I to O. Thus, we can test a database application by selecting values from I , executing the application on them, and checking whether the resulting values from O agree with the speci c ...
Assembling Metadata for Database Forensics.
... the DBMS was compromised can be considered to be clean application data. Using a data dump of the compromised DBMS requires that the investigator confirm that the data in each record is correct. Because of this complication, a forensic investigation of Scenario 0000 will be rare. However, the proces ...
... the DBMS was compromised can be considered to be clean application data. Using a data dump of the compromised DBMS requires that the investigator confirm that the data in each record is correct. Because of this complication, a forensic investigation of Scenario 0000 will be rare. However, the proces ...
Oracle Database 10g: Best for Windows
... Source: IDC November 2004. The RDBMS Top 10: License Sales Analysis and Market Forecast, 2003.2008 ...
... Source: IDC November 2004. The RDBMS Top 10: License Sales Analysis and Market Forecast, 2003.2008 ...
CH 10
... and by defining transaction boundaries. – Using menus, the developer may control the access for a particular user. This access may change throughout a user’s ...
... and by defining transaction boundaries. – Using menus, the developer may control the access for a particular user. This access may change throughout a user’s ...
Databases, Data, and Information
... Database Administration Database analysts and administrators are responsible for managing and coordinating all database activities Database Analyst (DA) Decides on proper field placement, defines data relationship, and identifies users’ ...
... Database Administration Database analysts and administrators are responsible for managing and coordinating all database activities Database Analyst (DA) Decides on proper field placement, defines data relationship, and identifies users’ ...
Database Management
... Database Administration Database analysts and administrators are responsible for managing and coordinating all database activities Database Analyst (DA) Decides on proper field placement, defines data relationship, and identifies users’ ...
... Database Administration Database analysts and administrators are responsible for managing and coordinating all database activities Database Analyst (DA) Decides on proper field placement, defines data relationship, and identifies users’ ...
Travel agency - mminfotek.com
... Some commercially available RDBMS are MS SQL Server, MS ACCESS, INGRES, ORACLE, and Sybase. MySQL, the most popular Open Source SQL database management system, is developed, distributed, and supported by Oracle Corporation. MySQL is named after co-founder Monty Widenius's daughter, My. The name of t ...
... Some commercially available RDBMS are MS SQL Server, MS ACCESS, INGRES, ORACLE, and Sybase. MySQL, the most popular Open Source SQL database management system, is developed, distributed, and supported by Oracle Corporation. MySQL is named after co-founder Monty Widenius's daughter, My. The name of t ...
Database Management Systems
... Database Administration Database analysts and administrators are responsible for managing and coordinating all database activities Database Analyst (DA) Decides on proper field placement, defines data relationship, and identifies users’ ...
... Database Administration Database analysts and administrators are responsible for managing and coordinating all database activities Database Analyst (DA) Decides on proper field placement, defines data relationship, and identifies users’ ...
10 Simple Steps for Boosting Database Performance in
... is passé. Even if there is a 10–20% overhead (and I’m inclined to say it’s closer to 10), with cheap hardware these days, the benefits far outweigh the negatives—just spend a little more and get a bigger server to handle multiple databases. But it may be a few years before this opinion is more widel ...
... is passé. Even if there is a 10–20% overhead (and I’m inclined to say it’s closer to 10), with cheap hardware these days, the benefits far outweigh the negatives—just spend a little more and get a bigger server to handle multiple databases. But it may be a few years before this opinion is more widel ...
Chapter 9: Object-Relational Databases
... • Extend the relational data model by including object orientation and constructs to deal with added data types. • Allow attributes of tuples to have complex types, including non-atomic values such as nested relations. • Preserve relational foundations, in particular the declarative access to data, ...
... • Extend the relational data model by including object orientation and constructs to deal with added data types. • Allow attributes of tuples to have complex types, including non-atomic values such as nested relations. • Preserve relational foundations, in particular the declarative access to data, ...
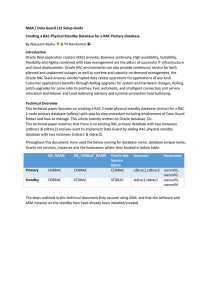
MAA / Data Guard 12c Setup Guide Creating a RAC Physical
... Implemented Maximum Availability Architecture (MAA) configuration for RAC primary database with RAC physical standby database using Oracle Data Guard and tested the configuration with objects. The goal of Maximum Availability Architecture (MAA) is to achieve optimal high availability for Oracle cust ...
... Implemented Maximum Availability Architecture (MAA) configuration for RAC primary database with RAC physical standby database using Oracle Data Guard and tested the configuration with objects. The goal of Maximum Availability Architecture (MAA) is to achieve optimal high availability for Oracle cust ...
Database-Friendly Security
... Award-Winning Database Monitoring with Minimal Overhead McAfee Database Activity Monitoring monitors all database activity in real-time based on pre-defined or custom rules and policies. It issues alerts on suspicious activity and prevents intrusion by terminating sessions that violate security poli ...
... Award-Winning Database Monitoring with Minimal Overhead McAfee Database Activity Monitoring monitors all database activity in real-time based on pre-defined or custom rules and policies. It issues alerts on suspicious activity and prevents intrusion by terminating sessions that violate security poli ...
An Approach Finding the Right Tolerance Level for Clinical Data Acceptance
... Queries are small programs created to perform comparisons of source data points to that which is in the database. Most clinical database management systems are equipped with query languages for building Edit Check programs. The programs are simple with a few basic constructs like (CREATE, SELECT, FR ...
... Queries are small programs created to perform comparisons of source data points to that which is in the database. Most clinical database management systems are equipped with query languages for building Edit Check programs. The programs are simple with a few basic constructs like (CREATE, SELECT, FR ...