Transactions
... transaction's read attempts. This may cause the first transaction to read two different values for the same data, causing the original read to be non-repeatable Phantom Reads occur when one transaction accesses a range of data more than once and a second transaction inserts or deletes rows that fall ...
... transaction's read attempts. This may cause the first transaction to read two different values for the same data, causing the original read to be non-repeatable Phantom Reads occur when one transaction accesses a range of data more than once and a second transaction inserts or deletes rows that fall ...
sql – structured query language
... keys are called candidate keys. The candidate key constraint indicates that the table cannot contain two different rows with the same values under candidate key columns. • foreign keys (referential integrity): Many a times, it is necessary to include column names from one table in another table. Exa ...
... keys are called candidate keys. The candidate key constraint indicates that the table cannot contain two different rows with the same values under candidate key columns. • foreign keys (referential integrity): Many a times, it is necessary to include column names from one table in another table. Exa ...
The Design of an Interactive Computer Assisted System To
... I would like to thank all members of the CAMIS team for the friendly cooperation during the research phase, the feasibility study and the design of the CAMIS application. In particular I want to thank my advisor Dr. Andreas Holzinger for his continuous and indefatigable support and for correcting al ...
... I would like to thank all members of the CAMIS team for the friendly cooperation during the research phase, the feasibility study and the design of the CAMIS application. In particular I want to thank my advisor Dr. Andreas Holzinger for his continuous and indefatigable support and for correcting al ...
Sample Profile Providers
... parameter name, the ADO.NET database type, and the size (i.e. length) that should be used with the ADO.NET parameter. The sample Profile property configuration shown above defines the following behavior when used with the SqlStoredProcedureProfileProvider. 1. The FirstName Profile property is define ...
... parameter name, the ADO.NET database type, and the size (i.e. length) that should be used with the ADO.NET parameter. The sample Profile property configuration shown above defines the following behavior when used with the SqlStoredProcedureProfileProvider. 1. The FirstName Profile property is define ...
courses
... Intermediate C#.NET programming. It is assumed that the student knows the C#.NET syntax as well as basic object oriented concepts. Teaches client-server systems, n-tier development environments, relational databases, use of SQL to access data, and use of ADO.NET objects, methods, and properties to a ...
... Intermediate C#.NET programming. It is assumed that the student knows the C#.NET syntax as well as basic object oriented concepts. Teaches client-server systems, n-tier development environments, relational databases, use of SQL to access data, and use of ADO.NET objects, methods, and properties to a ...
An Introduction to Object-Oriented Systems Analysis and
... – The database management system searches the database for Joe Soap, and – Returns his address to the COBOL program Copyright © 2004 by The McGraw-Hill Companies, Inc. All rights reserved. ...
... – The database management system searches the database for Joe Soap, and – Returns his address to the COBOL program Copyright © 2004 by The McGraw-Hill Companies, Inc. All rights reserved. ...
Lab07_Triggers
... INSERT, UPDATE and DELETE. The before/after options can be used to specify when the trigger body should be fired with respect to the triggering statement. If the user indicates a BEFORE option, then Oracle fires the trigger before executing the triggering statement. On the other hand, if an AFTER is ...
... INSERT, UPDATE and DELETE. The before/after options can be used to specify when the trigger body should be fired with respect to the triggering statement. If the user indicates a BEFORE option, then Oracle fires the trigger before executing the triggering statement. On the other hand, if an AFTER is ...
TRIGGER trigger_name
... INSERT, UPDATE and DELETE. The before/after options can be used to specify when the trigger body should be fired with respect to the triggering statement. If the user indicates a BEFORE option, then Oracle fires the trigger before executing the triggering statement. On the other hand, if an AFTER is ...
... INSERT, UPDATE and DELETE. The before/after options can be used to specify when the trigger body should be fired with respect to the triggering statement. If the user indicates a BEFORE option, then Oracle fires the trigger before executing the triggering statement. On the other hand, if an AFTER is ...
Database Security and Auditing
... DML Auditing Using Repository with Oracle (Simple 2) (continued) • Steps: – Use any user other than SYSTEM or SYS; with privileges to create tables, and triggers – Create the auditing repository – Establish a foreign key in AUDIT_DATA table referencing AUDIT_TABLE table – Create a sequence object – ...
... DML Auditing Using Repository with Oracle (Simple 2) (continued) • Steps: – Use any user other than SYSTEM or SYS; with privileges to create tables, and triggers – Create the auditing repository – Establish a foreign key in AUDIT_DATA table referencing AUDIT_TABLE table – Create a sequence object – ...
Application Context
... A global Application Context Is there a simple way to maintain and access the application context from everywhere it’s needed? a) ...
... A global Application Context Is there a simple way to maintain and access the application context from everywhere it’s needed? a) ...
Sample Chapter 5 (PDF, 60 Pages
... It had been more work than Marla thought, but she had finally finished upgrading the existing computers in The 1881 and initiated a tablet loaner program where guests could borrow an iPad to use during their stay. Fresh from this success, Marlo’s next move was to get a better idea of the guests who ...
... It had been more work than Marla thought, but she had finally finished upgrading the existing computers in The 1881 and initiated a tablet loaner program where guests could borrow an iPad to use during their stay. Fresh from this success, Marlo’s next move was to get a better idea of the guests who ...
Database Deployment scenarios and performance on SSD arrays
... I/O. While parallel processing and increased RAM can address some performance issues, ultimate performance figures are dictated by how fast data can be moved to/from the storage ...
... I/O. While parallel processing and increased RAM can address some performance issues, ultimate performance figures are dictated by how fast data can be moved to/from the storage ...
Intro to DB2 UDB Programming Using REXX
... DB2 is a client-server database, so you can install a small DB2 client on your platform, which connects over the network (typically TCP/IP) to DB2 running on another host. The personal editions of DB2 allow you to have a DB2 server and client on the same host for development purposes. DB2 is a multi ...
... DB2 is a client-server database, so you can install a small DB2 client on your platform, which connects over the network (typically TCP/IP) to DB2 running on another host. The personal editions of DB2 allow you to have a DB2 server and client on the same host for development purposes. DB2 is a multi ...
New Database Design for the APS Survey and Alignment Data
... 2.3.1 Functional Dependencies and Normalization Analysis of the functional dependencies (FDs) within a database is one of the essential tools for working with relations and the process of normalization. Functional dependency is a term describing a situation, when one attribute or a set of attribute ...
... 2.3.1 Functional Dependencies and Normalization Analysis of the functional dependencies (FDs) within a database is one of the essential tools for working with relations and the process of normalization. Functional dependency is a term describing a situation, when one attribute or a set of attribute ...
Slide 1
... Problems & Requirements, Part 1: What Customers Asked For • Even in Oracle9i customers wanted a metadata comparison tool: “I want you to compare the metadata for two tables (in different databases), show me if they’re different, and give me the ALTER commands to make one like the other.” ...
... Problems & Requirements, Part 1: What Customers Asked For • Even in Oracle9i customers wanted a metadata comparison tool: “I want you to compare the metadata for two tables (in different databases), show me if they’re different, and give me the ALTER commands to make one like the other.” ...
2. SDMX Istat framework
... to publish a RSS file that informs when new data is loaded or updated, which then specifies the URL where to find the files containing the SDMX Query which then locates the new or updated data; to publish one or more SDMX Query file(s); to publish one or more SDMX Compact file(s) (optional). T ...
... to publish a RSS file that informs when new data is loaded or updated, which then specifies the URL where to find the files containing the SDMX Query which then locates the new or updated data; to publish one or more SDMX Query file(s); to publish one or more SDMX Compact file(s) (optional). T ...
Databases
... Move your mouse over the terms of the following interaction and get to know what parts make up an information system. Only pictures can be viewed in the PDF version! For Flash etc. see online version. Only screenshots of animations will be displayed. [link] The data managements components of an info ...
... Move your mouse over the terms of the following interaction and get to know what parts make up an information system. Only pictures can be viewed in the PDF version! For Flash etc. see online version. Only screenshots of animations will be displayed. [link] The data managements components of an info ...
Additional Considerations for SQL Server 2012 Databases
... military applications. Consumer privacy requirements are yet another emerging driver for finer control of data. The typical approach to meeting such requirements in database applications has been to implement the necessary logic in application code. The business logic layer of an ntier application m ...
... military applications. Consumer privacy requirements are yet another emerging driver for finer control of data. The typical approach to meeting such requirements in database applications has been to implement the necessary logic in application code. The business logic layer of an ntier application m ...
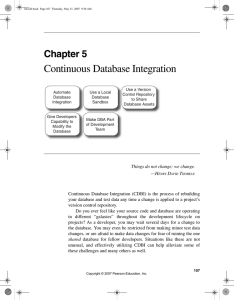
Continuous Database Integration
... discuss which database files are committed to a version control repository. Automating a database integration build process solves only part of the problem, so we go one step further by rebuilding the database and data at every software change—making the verification process continuous. If a team is ...
... discuss which database files are committed to a version control repository. Automating a database integration build process solves only part of the problem, so we go one step further by rebuilding the database and data at every software change—making the verification process continuous. If a team is ...
Microsoft System
... Protect or recover the whole machine No data select-ability / granularity “Bare Metal Recovery” of every VM Single DPM license on host, all guests protected Protect non-Windows servers One DPML “agent” on Host ...
... Protect or recover the whole machine No data select-ability / granularity “Bare Metal Recovery” of every VM Single DPM license on host, all guests protected Protect non-Windows servers One DPML “agent” on Host ...