Generating the Server Response: HTTP Status Codes
... – Names derived from standard message. E.g., SC_OK, SC_NOT_FOUND, etc. ...
... – Names derived from standard message. E.g., SC_OK, SC_NOT_FOUND, etc. ...
Page - MarcelaPineros.com
... Web Browsers read hypertext markup language to allow users to view web pages and navigate the internet through a system of links: Netscape and Internet Explorer are web browsers Search Engines are database tools that search the contents of the internet to find pages or sites that contain information ...
... Web Browsers read hypertext markup language to allow users to view web pages and navigate the internet through a system of links: Netscape and Internet Explorer are web browsers Search Engines are database tools that search the contents of the internet to find pages or sites that contain information ...
Top Technologies & Trends
... that are appropriate to your mission Imaginatively apply those technologies to serve the unique needs of your users Provide easy access to what they want, how and when they want it Market those services well Rinse and repeat ...
... that are appropriate to your mission Imaginatively apply those technologies to serve the unique needs of your users Provide easy access to what they want, how and when they want it Market those services well Rinse and repeat ...
The Internet - Mr. Rydalch
... Examples of browsers are Netscape, Microsoft Internet Explorer, Mosaic, Mac web, and Net cruiser. ...
... Examples of browsers are Netscape, Microsoft Internet Explorer, Mosaic, Mac web, and Net cruiser. ...
How the Web Works
... • Default files are used to identify the first page the browser displays per directory. https:// is a secure server transaction. Secure servers have special encryption devices that hide delicate content, such as credit card numbers, while they are transferred to and from the browser. ...
... • Default files are used to identify the first page the browser displays per directory. https:// is a secure server transaction. Secure servers have special encryption devices that hide delicate content, such as credit card numbers, while they are transferred to and from the browser. ...
WebReport
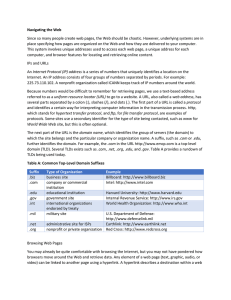
... Since so many people create web pages, the Web should be chaotic. However, underlying systems are in place specifying how pages are organized on the Web and how they are delivered to your computer. This system involves unique addresses used to access each web page, a unique address for each computer ...
... Since so many people create web pages, the Web should be chaotic. However, underlying systems are in place specifying how pages are organized on the Web and how they are delivered to your computer. This system involves unique addresses used to access each web page, a unique address for each computer ...
CS 195 Web Development I
... is not WP or DTP Can’t control page size Little font & size control Limited control of position of graphics Why these limitations? ...
... is not WP or DTP Can’t control page size Little font & size control Limited control of position of graphics Why these limitations? ...
Voc #4
... portals provide access to information that is organized along vertical market sectors. That is, focused on particular topics instead of a broadly, horizontally, range of topics. ...
... portals provide access to information that is organized along vertical market sectors. That is, focused on particular topics instead of a broadly, horizontally, range of topics. ...
Web Security Crash Course
... Exploits trust that servers place in browsers It’s very difficult for a web server to know whether a request your computer sent it was sent with your knowledge or approval Different than XSS, but XSS is often an attack vector for CSRF ...
... Exploits trust that servers place in browsers It’s very difficult for a web server to know whether a request your computer sent it was sent with your knowledge or approval Different than XSS, but XSS is often an attack vector for CSRF ...
Creating Web Pages
... Use lowercase for tags & attributes Quote attribute values Use relative references for resources on same server Always use closing tags Nest elements properly; close in reverse order of opening Use indentation consistently and to make code readable No more than 80 characters per line of code; break ...
... Use lowercase for tags & attributes Quote attribute values Use relative references for resources on same server Always use closing tags Nest elements properly; close in reverse order of opening Use indentation consistently and to make code readable No more than 80 characters per line of code; break ...
Document
... • What does the company do, can the user tell this from the front page • Contact information on every page ...
... • What does the company do, can the user tell this from the front page • Contact information on every page ...
ppt
... content for grammatical or spelling errors ► Test all links to ensure integrity of site navigation and external links ► Access site by typing in URL rather than viewing page through site editor ...
... content for grammatical or spelling errors ► Test all links to ensure integrity of site navigation and external links ► Access site by typing in URL rather than viewing page through site editor ...
Scavenger Hunt - Schlaffman
... • Browser - A program used to view HTML documents…ex: Internet Explorer, Firefox • Website -A collection of web pages, or a collection of links between pages…Schlaffman Wiki • URL -The address of a web page on the world wide web Ex: www.schlaffman.wikispaces.com ...
... • Browser - A program used to view HTML documents…ex: Internet Explorer, Firefox • Website -A collection of web pages, or a collection of links between pages…Schlaffman Wiki • URL -The address of a web page on the world wide web Ex: www.schlaffman.wikispaces.com ...
Presentation - fudgelink.com
... • Goodies such as e-mail accounts, FTP, forums and chat, streaming audio and video support, submission to search engines, more ...
... • Goodies such as e-mail accounts, FTP, forums and chat, streaming audio and video support, submission to search engines, more ...
Web Design
... • Make sure that users can get where they need to go within your site quickly and easily. • Make sure the navigational elements will work in a non-graphical browser as well as in a rich format. ...
... • Make sure that users can get where they need to go within your site quickly and easily. • Make sure the navigational elements will work in a non-graphical browser as well as in a rich format. ...
Web Patterns
... their time on other sites, so that's where they form their expectations for how the Web works. Test your design with real users as a reality check. People do things in odd and unexpected ways, so even the most carefully planned project will learn from usability testing. ...
... their time on other sites, so that's where they form their expectations for how the Web works. Test your design with real users as a reality check. People do things in odd and unexpected ways, so even the most carefully planned project will learn from usability testing. ...
Our Solution
... (View/Toolbars/Drawing || Draw -> Align). It’s cool. • View at 100% to see how BIG it will be when done ...
... (View/Toolbars/Drawing || Draw -> Align). It’s cool. • View at 100% to see how BIG it will be when done ...
HTML and Game Maker Studio
... Type “telnet google.com 80” Press “Enter” Type “GET” Press “Enter” ...
... Type “telnet google.com 80” Press “Enter” Type “GET” Press “Enter” ...
Wrappers
... corresponding to DOM location stored in current smart bookmark step. If the link exists, the target of the link matches the bookmark, and either the URL or text of the retrieved link match the step, then use that link. - Otherwise, if there is a unique link in the page whose target, URL, and text ma ...
... corresponding to DOM location stored in current smart bookmark step. If the link exists, the target of the link matches the bookmark, and either the URL or text of the retrieved link match the step, then use that link. - Otherwise, if there is a unique link in the page whose target, URL, and text ma ...
ppt
... ucsd.edu/form.cgi using HTTPS. Onlookers may not view the password. • (3 pts) Write HTML code that uses Javascript to write “Hello World!” to the browser window. • (2 pts) Write a Javascript function that takes two numbers and returns their sum. • (2 pts) Using Javascript to access the DOM, access t ...
... ucsd.edu/form.cgi using HTTPS. Onlookers may not view the password. • (3 pts) Write HTML code that uses Javascript to write “Hello World!” to the browser window. • (2 pts) Write a Javascript function that takes two numbers and returns their sum. • (2 pts) Using Javascript to access the DOM, access t ...
The Internet I 1/2 - SEE-ICT
... must have internet security software installed on all computers at home. ...
... must have internet security software installed on all computers at home. ...
Websynergies - Search Engine Optimization (SEO)
... - Using a reasonably-sized, accurate description meta tag without excessive use of keywords, exclamation marks or off topic terms. - Ensuring that all pages are accessible via anchor tag hyperlinks, and not only via Java, Javascript or Macromedia Flash applications or meta refresh redirection; this ...
... - Using a reasonably-sized, accurate description meta tag without excessive use of keywords, exclamation marks or off topic terms. - Ensuring that all pages are accessible via anchor tag hyperlinks, and not only via Java, Javascript or Macromedia Flash applications or meta refresh redirection; this ...