XML Security Standards — Overview for the Non - Events
... Defines generic Security Token Service (STS) Issue, renew, cancel, validate Tokens Support for many different configurations and trust relationships Only defines generic elements Other specifications intended to extend and specify the details, ...
... Defines generic Security Token Service (STS) Issue, renew, cancel, validate Tokens Support for many different configurations and trust relationships Only defines generic elements Other specifications intended to extend and specify the details, ...
Controls
... Password management routines such as requiring periodic password changes, quality passwords, longer passwords, etc. ...
... Password management routines such as requiring periodic password changes, quality passwords, longer passwords, etc. ...
Secure your remote access with VASCO and
... Combining Juniper Networks’ firewalls, VPN solutions and network access security appliances with VASCO’s DIGIPASS strong authentication enhances the security of your network and remote access, while remaining easy-to-use When employees use their PC, they want to read e-mail, use software and documen ...
... Combining Juniper Networks’ firewalls, VPN solutions and network access security appliances with VASCO’s DIGIPASS strong authentication enhances the security of your network and remote access, while remaining easy-to-use When employees use their PC, they want to read e-mail, use software and documen ...
Chapter X Slides
... • Only the corresponding public-key can decrypt the message that is encrypted with the private-key • Only the corresponding private-key can decrypt the message that is encrypted with the public-key • Has a one-to-one relationship between keys ...
... • Only the corresponding public-key can decrypt the message that is encrypted with the private-key • Only the corresponding private-key can decrypt the message that is encrypted with the public-key • Has a one-to-one relationship between keys ...
Slide 1
... Comprehending the Security Process Implementing Access Control The Discretionary Access Control model (DAC) The Discretionary Access Control model (DAC) is used in small Microsoft workgroup networks where users commonly share folders with each other. In the DAC model, the data owner\creator is resp ...
... Comprehending the Security Process Implementing Access Control The Discretionary Access Control model (DAC) The Discretionary Access Control model (DAC) is used in small Microsoft workgroup networks where users commonly share folders with each other. In the DAC model, the data owner\creator is resp ...
Security
... – Merchant then signs message by encrypting with their private key – Customer decrypts using the merchants public key to prove authenticity of sender – Customer decrypts using their private key to ensure integrity of message ...
... – Merchant then signs message by encrypting with their private key – Customer decrypts using the merchants public key to prove authenticity of sender – Customer decrypts using their private key to ensure integrity of message ...
Database Security
... organization’s intranet from unauthorized access • Ensures that messages entering or leaving intranet meet the organization’s standards • Packet filter examines each packet of information before it enters or leaves the intranet • Gateway techniques can apply security mechanisms to applications or co ...
... organization’s intranet from unauthorized access • Ensures that messages entering or leaving intranet meet the organization’s standards • Packet filter examines each packet of information before it enters or leaves the intranet • Gateway techniques can apply security mechanisms to applications or co ...
Three challenges with secret key encryption
... Step4: The user types this response and sends it to the Authentication server. While the user is obtaining a response from the token, the Authentication server calculates what the appropriate response should be based on its database of user keys. Step5: When the server receives the user’s response, ...
... Step4: The user types this response and sends it to the Authentication server. While the user is obtaining a response from the token, the Authentication server calculates what the appropriate response should be based on its database of user keys. Step5: When the server receives the user’s response, ...
Chapter 9
... Remote Access – Dial up clients and Internet access from private networks Both sides require a shared IPSec policy to establish the ...
... Remote Access – Dial up clients and Internet access from private networks Both sides require a shared IPSec policy to establish the ...
FTAA Joint Public-Private Sector Committee of Experts
... the transformation of data in order to hide its information content, establish its authenticity, prevent its undetected modification, its repudiation and unauthorized use. It can be used to protect the confidentiality of data whether in storage or in transit. A variety of applications have been deve ...
... the transformation of data in order to hide its information content, establish its authenticity, prevent its undetected modification, its repudiation and unauthorized use. It can be used to protect the confidentiality of data whether in storage or in transit. A variety of applications have been deve ...
Digital Billboard Security Guidelines
... Intrusion Detection System (IDS): An IDS will monitor computer network communications to identify potentially malicious traffic. The actions taken by an IDS could be to simply alert security personnel to the communications or to block the communications to protect the billboard. Multi-factor Authent ...
... Intrusion Detection System (IDS): An IDS will monitor computer network communications to identify potentially malicious traffic. The actions taken by an IDS could be to simply alert security personnel to the communications or to block the communications to protect the billboard. Multi-factor Authent ...
Replacing Tripwire with SNMPv3 DefConX Presentation 08/02/02
... Services through query of Provider "Engine ID" also important Engine ID provides significant security addition through first pass hash ...
... Services through query of Provider "Engine ID" also important Engine ID provides significant security addition through first pass hash ...
Securing Distribution Automation
... The availability of an enterprise uplink can generally not be ensured at all times and a local authentication solution is still required. To fulfill this requirement, some vendors provide an innovative mechanism where a remote access server grants the user a limited duration “security ticket” that ...
... The availability of an enterprise uplink can generally not be ensured at all times and a local authentication solution is still required. To fulfill this requirement, some vendors provide an innovative mechanism where a remote access server grants the user a limited duration “security ticket” that ...
Chapter 6
... • How firewalls can protect intranets and corporate servers • What role the Secure Socket Layer, Secure HTTP, and secure electronic transaction protocols play in protecting electronic commerce ...
... • How firewalls can protect intranets and corporate servers • What role the Secure Socket Layer, Secure HTTP, and secure electronic transaction protocols play in protecting electronic commerce ...
Web Server Administration
... E-mail can get denial of service if an overwhelming number of messages are sent at the same time Viruses can be sent to e-mail users User authentication done in plain text when Retrieving e-mail over the Internet ...
... E-mail can get denial of service if an overwhelming number of messages are sent at the same time Viruses can be sent to e-mail users User authentication done in plain text when Retrieving e-mail over the Internet ...
Net+ Chapter 1
... encrypted and decrypted during transmission. • Also, all of the data transmitted across the connection contains a mechanism to detect tampering, so the data can be checked to see if it was altered during the transfer process. ...
... encrypted and decrypted during transmission. • Also, all of the data transmitted across the connection contains a mechanism to detect tampering, so the data can be checked to see if it was altered during the transfer process. ...
Here is the Original File
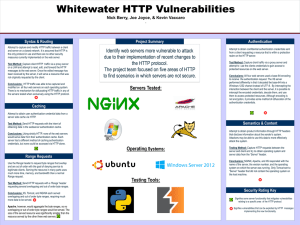
... and server on a closed network. It is assumed that HTTP is the only protocol in use and there are no other security measures currently implemented on the web server. Test Method: Capture client HTTP traffic via a proxy server on a LAN and attempt to read, edit, and forward the HTTP messages to the w ...
... and server on a closed network. It is assumed that HTTP is the only protocol in use and there are no other security measures currently implemented on the web server. Test Method: Capture client HTTP traffic via a proxy server on a LAN and attempt to read, edit, and forward the HTTP messages to the w ...
Chapter 19
... Handshake Protocol Phases • Phase 1: Initiates logical connection • Phase 2: passes certificate, additional key information and request for client certificate. Also passes server-done message. • Phase 3: client sends message to server depending on underlying public-key scheme. • Phase 4: completes ...
... Handshake Protocol Phases • Phase 1: Initiates logical connection • Phase 2: passes certificate, additional key information and request for client certificate. Also passes server-done message. • Phase 3: client sends message to server depending on underlying public-key scheme. • Phase 4: completes ...
Chapter 24 - William Stallings, Data and Computer
... provides the • can be implemented in routers or firewalls owned network and operated by the manager organization with • a service provider can simplify the job of planning, complete implementing, and control over maintaining Internet-based the security VPNs for secure access and aspects of secure co ...
... provides the • can be implemented in routers or firewalls owned network and operated by the manager organization with • a service provider can simplify the job of planning, complete implementing, and control over maintaining Internet-based the security VPNs for secure access and aspects of secure co ...
Chapter 32
... – Mutable fields are those IP headers that get changed in transit • We don’t want these slight changes to cause authentication errors • So IPsec will only authenticate the immutable fields ...
... – Mutable fields are those IP headers that get changed in transit • We don’t want these slight changes to cause authentication errors • So IPsec will only authenticate the immutable fields ...
Security - Glasnost
... The Biba Model • Principles to guarantee integrity of data 1. Simple integrity principle ...
... The Biba Model • Principles to guarantee integrity of data 1. Simple integrity principle ...
Security
... The Biba Model • Principles to guarantee integrity of data 1. Simple integrity principle ...
... The Biba Model • Principles to guarantee integrity of data 1. Simple integrity principle ...
Hardware Building Blocks and Encoding
... Internet for the telephone system as the underlying structure for communications. The trusted VPN components of the new VPN still do not offer security but they give customers a way to easily create network segments for wide area networks (WANs). On the other hand, the secure VPN components can be c ...
... Internet for the telephone system as the underlying structure for communications. The trusted VPN components of the new VPN still do not offer security but they give customers a way to easily create network segments for wide area networks (WANs). On the other hand, the secure VPN components can be c ...
Network Security For Distributed Simulation Systems
... 3: MS encrypts data with its private key and returns data to network ...
... 3: MS encrypts data with its private key and returns data to network ...